Website security is often insufficient and this can have really nasty consequences. Users have no influence on how a website handles the data they entrust to it. And unfortunately a lot of vulnerabilities on a website are not visible at the surface. One of many examples is password storage. Unless a website emails passwords in plain text we have no visible indication whether they are storing them in a cryptographically strong way.
Often we discover this only after they are effectively leaked on the internet or even after accounts are taken over by hackers. While we cannot change the website under the covers, there are some things we can have under control.
There are always cases where you are forced to use a particular website, but most of the times you have the ability to make a conscious decision about entrusting personal data to a website. And you should really do this. Be critical before you provide your data to a website!
Due to more coverage of security incidents in the media, people become more scared and consequently want to be better informed. And the question I often get is:
How can you know if a website is secure?
It may be disappointing, but the answer is simply that you can’t. 100% security is a myth. But this is the case for anything, not only for online applications. Actually this is not the right question to ask. So let’s rephrase it:
How can I build enough trust in a website before I start using it?
And this is where the shoe pinches. Although browsers (like Google Chrome) can help you to judge the reliability of a website, they can also cause confusion. As we will see later on, they can even have the opposite effect. That’s why it is really important to understand how browsers— I will limit myself in this article to Chrome — try to help the user by means of security indicators.
Security indications
HTTP websites
In the address bar of Chrome you get indications about the security of the connection with a particular website. Let’s see how this looks in chrome 55.
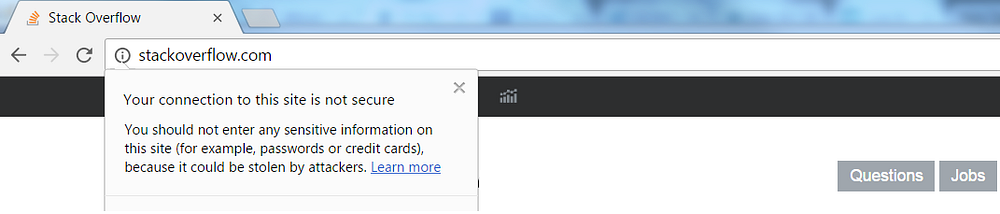
By clicking on the info icon in front of the url stackoverflow.com (actually the url is http://www.stackoverflow.com, but it is shortened by Chrome), you get the information depicted above. This notification is shown because the browser communicates with this website via the insecure Hypertext Transfer Protocol, better known as HTTP. As you can see, it’s advised not to enter passwords or any other sensitive information on this website because it can be stolen by attackers.
In chrome 56 this will be even more obvious:
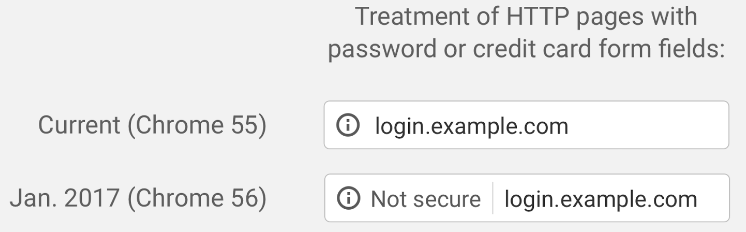
Note that this is only the case for websites that collect passwords and credit card numbers and use HTTP.
But this is a next step in the right direction. Fact is that, by nature, most people just want to create an account for an online service and don’t think too much about security of their data. They just want to start using it as quick as possible. This mark in the address bar will hopefully make them think twice before they entrust their sensitive data to a website served over HTTP.
Firefox 51 that’s recently released, does exactly the same as Chrome for HTTP websites collecting passwords. This explicit marking of non-secure websites is a good thing and will force a lot of websites to switch to HTTPS.
HTTPS websites
It might be clear by now that websites that deal with sensitive user data should make sure that they are transported securely between browser and website. The protocol that makes this possible is HTTPS.
HTTPS is the secure variant of HTTP. It adds an extra layer of security to the data in transit by means of the SSL (Secure Socket Layer) or TLS (Transport Layer Security) protocol.
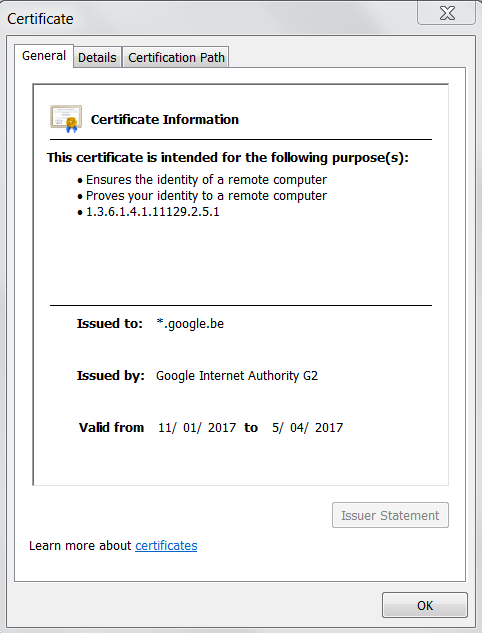
To enable HTTPS on a website a SSL certificate must be requested at a Certificate Authority (CA). This certificate must be installed on the server(s) hosting the website.
SSL certificates, sometimes called digital certificates, are used to establish a secure, encrypted connection between a browser and a server. The SSL connection protects sensitive data, like credit card information, during every visit to the website (session).
Although we are speaking here about SSL certificates and connections, SSL is an old and vulnerable protocol that is no longer supported by the current versions of the browsers. If we speak about HTTPS nowadays, we actually mean a connection secured by the TLS protocol.
Let’s have a look how chrome determines and shows if a HTTPS connection between a browser and a website is safe or not.
As an example we will take the website https://www.nespresso.be. Chrome shows very clearly that the site is ‘Not secure’. ‘https’ is also striked through in red. In the notification on the page the risks are clearly described. And these are exactly the same as for HTTP. The only difference is that Chrome has an extra protection built in for sites with broken HTTPS. By default, it doesn’t load insecure HTTPS pages.
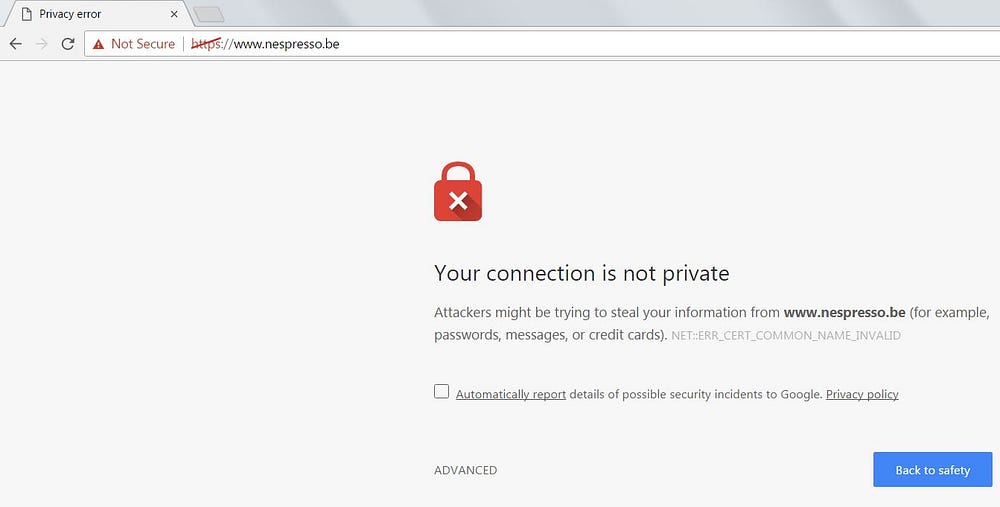
If we click on ‘Not secure’ in the address bar we get to see the details:
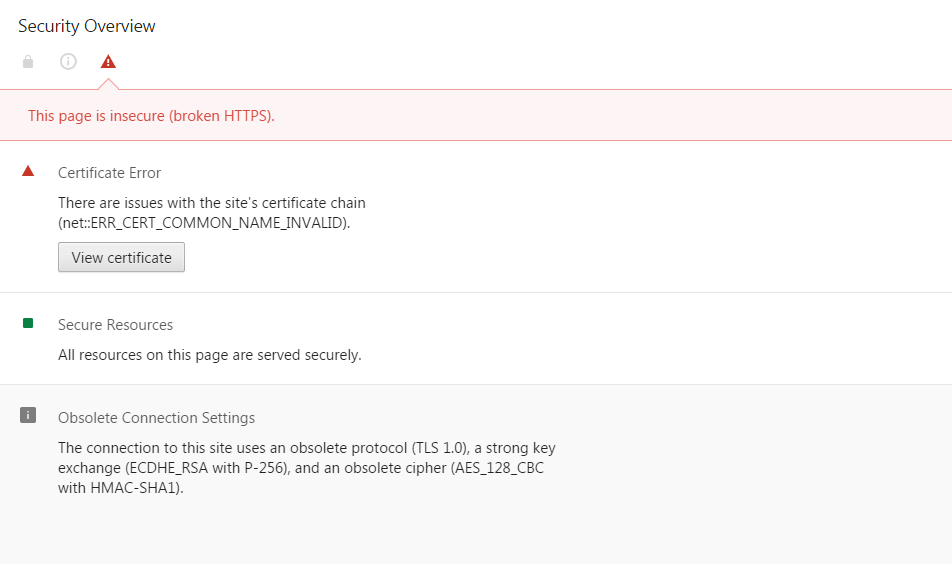
The HTTPS implementation is broken due to problems with the certificate and obsolete connection settings. A solution is to use TLS as mentioned earlier, but it must be a recent version. TLS 1.0 is a deprecated protocol with known vulnerabilities.
Let’s have a look at another notification that Chrome can show for a HTTPS website:
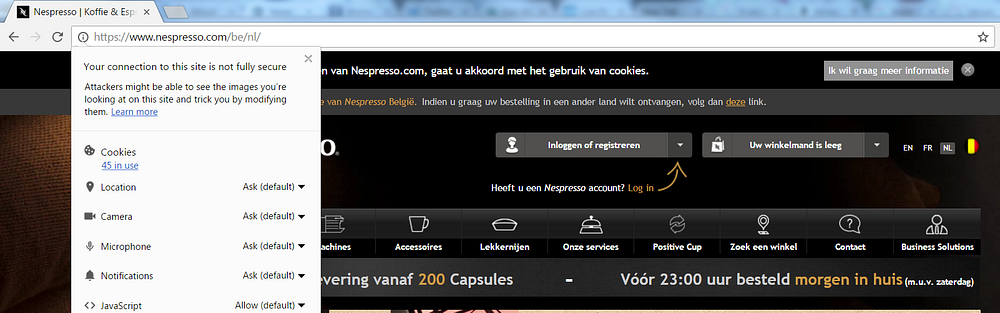
And indeed it’s the same info symbol in front of the url as we saw at the HTTP website. If we look at the details:
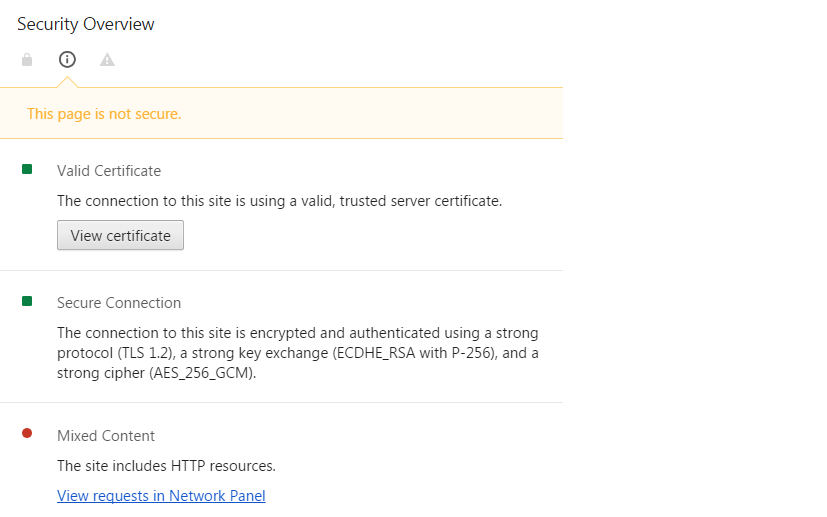
We see that in this case the certificate is valid and the connection is secured by TLS 1.2. But the reason that the site is marked as insecure is because it serves mixed content, in other words it includes HTTP resources. By clicking on the link the resource loaded over HTTP is shown.
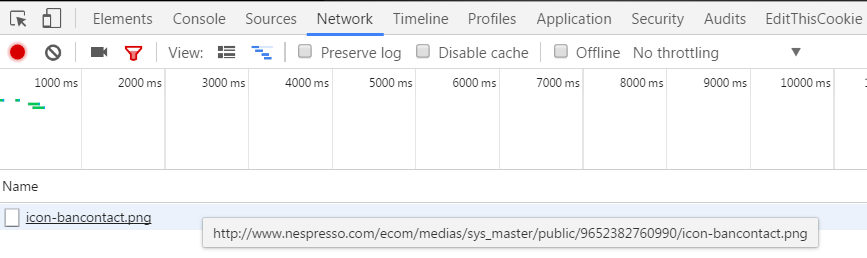
A website with mixed content is flagged as insecure because it establishes a man-in-the-middle attack risk. If you’re interested to learn more about the risks of mixed content have a look at this video from Troy Hunt.
Until now we saw websites over HTTP, which is inherently insecure, or over badly implemented HTTPS. Let’s have a look at a website that is marked as secure by Chrome.
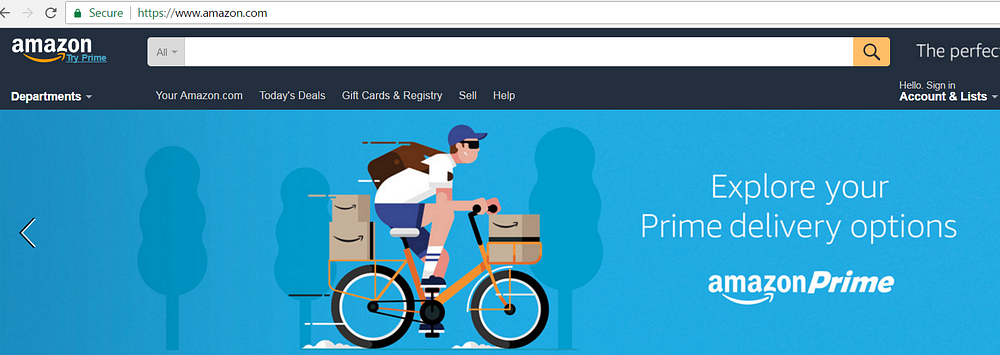
What this means is that the communication channel is secure. Your information is private when it is exchanged with Amazon. Another slightly different example of Chrome marking a website as secure is the next one:
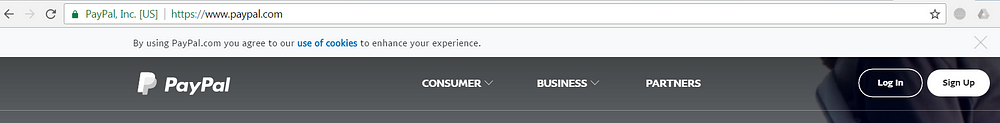
In the browser address bar we see a green padlock and ‘PayPal? Inc. [US]’. This is what we call an Extended Validation (EV) certificate. Its purpose is to give users more trust in the website. While you can request a SSL certificate without verification of your identity, to get an EV certificate you need to go through a rigorous identity verification process. It may be an extra level of trust but in practice, EV certificates are the exception rather than the rule.
This begs the question, is a site marked as secure by the browser always trustworthy?
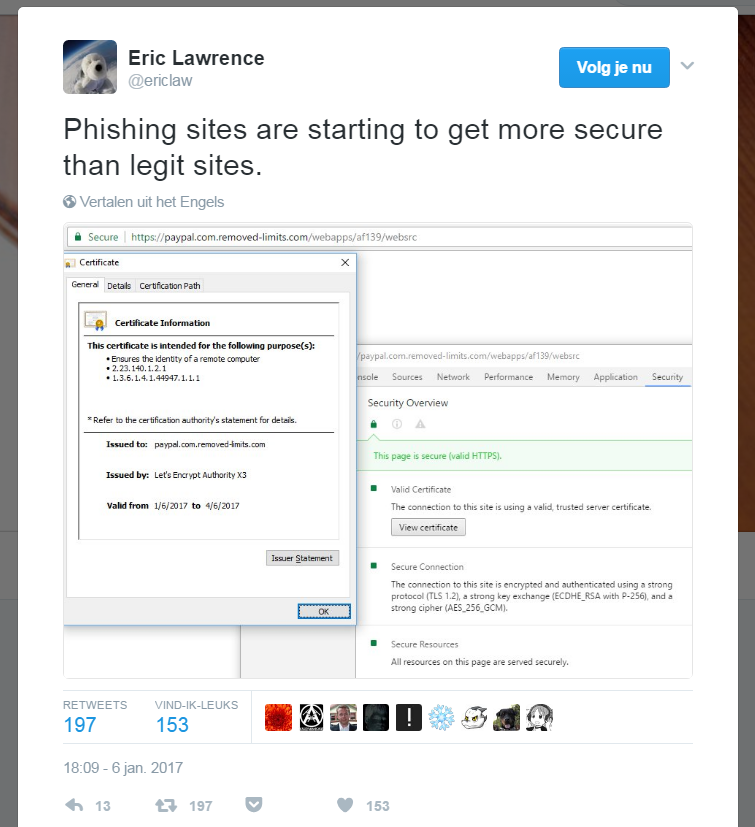
And the answer is simply ‘no’. What we see in the above tweet is a phishing site considered as secure by the browser. And this is where phishing will be particular effective. A lot of people still think that a site communicating over HTTPS can’t be a phishing site. Let’s be clear that this is a myth, and a dangerous one! You should always verify the domain in the url. If it’s not the official domain of the website it pretends to be, it’s a phishing site.
Conclusion
Browsers can help users a lot nowadays. They will show in the address bar if data is communicated between browser and website in a secure fashion. Marking websites as insecure is on the other hand a really good incentive to force websites to use HTTPS.
Understanding that it is not a good idea to use websites flagged as non-secure might be quite trivial for most people. But if for instance a phishing site is marked as secure by the browser, things are getting tricky. What people really need to understand is that a valid HTTPS implementation guarantees that the communication between the browser and the website is private and thus secure. It says nothing at all about what the website does with the data you give it. A secure phishing site is still a phishing site. So always check if the url is in the known valid domain of that website. An EV certificate like we saw in the PayPal example, is also a strong indication the website is trustworthy.