Recently I ran a questionnaire that covers several security aspects. One of the questions was:
‘Do you ever check if sensitive personal data is leaked on the web?’
7 out of 10 people answered ‘no’. The reason? Either they haven't thought about doing it or they simply don’t know where to find this kind of information.
Most people that answered ‘yes’ sometimes google their name to see what information is publicly available about them. And it is definitely a good idea to do this once in a while. If you find sensitive personal information you can request the search engine to remove it. And I strongly advice you to do this. Because if you can find this information, anyone in the world can, also people with malicious intents.
While a google search can help, it often shows only the tip of the iceberg. Private data are often leaked after a data breach happens. Wikipedia defines a data breach as follows:
“A data breach is a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an individual unauthorized to do so.”
Unfortunately it is not that common to find your breached data with a google search. Unless something really bad like this happens. In short, tens of thousands of pathology files of Indians were publicly accessible and easily discoverable because they where indexed by google. All that was needed was a simple google search with an “inurl”.
As it seems, a lot of people have no idea how they can check whether they are victim of a particular data breach. Best case scenario is that the breached company discloses the breach to its customers (so they will be aware). But unfortunately a lot of data breaches happen without the affected users being notified.
Even if people are informed by the breached company, a lot of them don’t realize the possible risks they are exposed to and what they can (and should) do to defend themselves.
How can you know if your data is leaked on the web?
Like I mentioned in the introduction, some companies do not take responsibility when they are breached. That’s why we need other resources to check if our data is leaked. Of course you could go and search on the dark web or download publicly leaked dumps of data breaches and check if your account is in there.
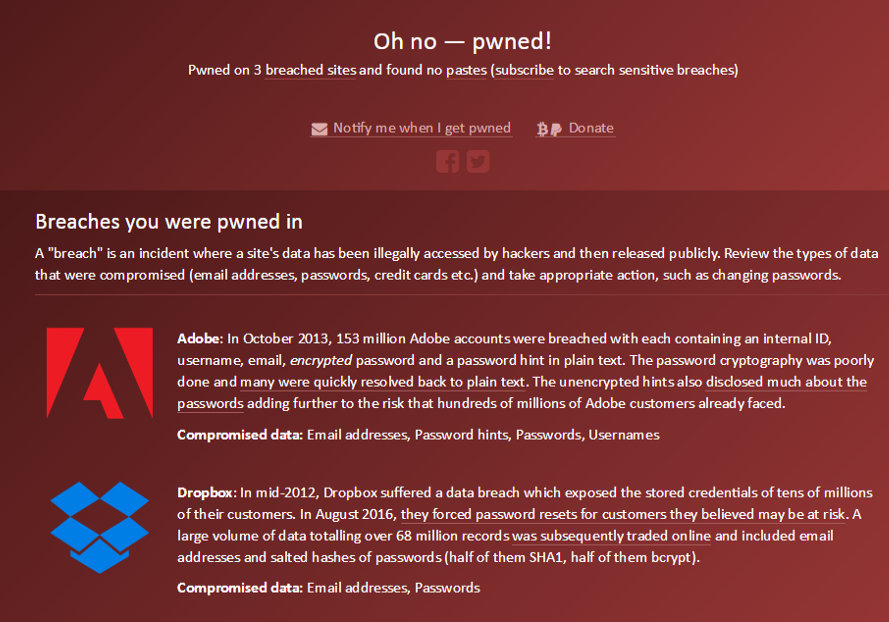
But there is a much better alternative, Have I Been Pwned? This a website created by Troy Hunt. It makes it really easy to check if your personal data has been compromised. Just type your e-mail address and click on the ‘pwned?’ button and you will see every data breach where your e-mail address appears in. For each of them there is a detailed explanation and a list of compromised data.
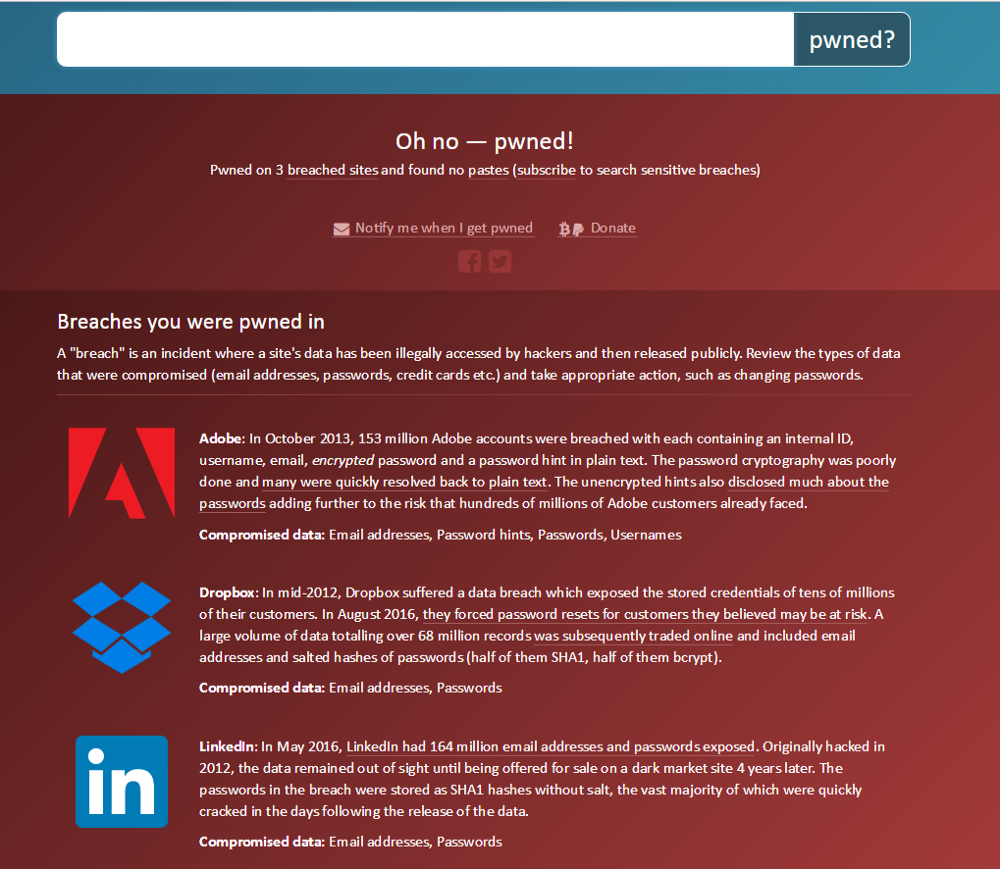
Another really neat feature of haveibeenpwned is the notification service. Subscribing is as easy as entering your e-mail address. From now on you will be notified every time a data breach containing your e-mail is added to the system.
Some password managers will also inform you when your account is breached. Later in this article I will talk in more detail about what makes password managers a good choice.
My account is breached, what now?
When you get to know that one of your accounts is breached, most important are the next steps you take. Let’s suppose you were victim of the Dropbox data breach in 2012 just like me.
The moment you learn about this it is important to understand the impact. Is your Dropbox account the only one that is in danger? Or do you reuse that password and where do you reuse it? If your password is leaked from one breach all your other accounts reusing this password are in danger. Even the ones you don’t remember you ever created!
So, the first thing to do, is changing your Dropbox password into a really strong unique password. Also enable ‘two step verification’ as an extra security measure. Adding a second authentication step makes it a lot harder for hackers to access your account (even if they have your password). A lot of services — like Dropbox — offer this possibility nowadays. But let’s be really clear that two step verification is never an excuse for password reuse.
Okay, now you mitigated the risk for Dropbox. But if you reused the password you have to change it for each and every website you did. Important again is that you create a strong and unique password for each account. And this is what people typically find hard. Choosing and remembering strong passwords. So instead they choose easy — in the best case different — passwords for their accounts.
This is where a password manager can help you. A password manager is a tool to securely store your passwords and often other sensitive data. The only password you need to remember is the master password (which must be a strong one) and the password manager will remember all the other passwords for you. This means that you can use strong random passwords without the fear of forgetting them.
Most password managers offer a lot of handy features like login automation in the browser, strong password generation, breach notification and often many more. Good password managers also have apps available for the different mobile operating systems.
Conclusion
The majority of people does not know how to check if confidential personal data are publicly exposed. Googling yourself regularly is certainly a good idea, but only shows a part of your private data floating around the web.
Data breaches often result in private data being leaked. So, have a look at Have I Been Pwned? and perform a search to see which of your accounts are compromised. Or even better subscribe to the breach notification service.
Password reuse puts all the accounts (and private data associated with them) at risk, not only the breached account. That’s why you should assess your password management strategy and if necessary change it to be as strong as possible. Remember that the strongest passwords are the ones you cannot remember. A password manager is designed exactly to accomplish that.
Besides increasing security, good password managers also increase efficiency both on desktop and mobile devices. Some of them can even warn you when one of your accounts is in a breach.
It will be clear by now that my advice is to use a password manager. In any case never reuse passwords, can we agree on that?