Ashar Javed had an interesting idea to create security awareness quiz questions and asked me if I wanted to cooperate. The idea is to make this a community effort and make these questions available for everyone. These questions are not intended for security professionals but for the average computer user.
Here's a first selection of questions by Ashar and me as an example. We hope together with you we can make this a great resource that can be used by many people and will help to spread security awareness. If you want to contribute either contact Ashar or me or leave a reply in the comments of this post. We'll update this post regularly.
Note: The name of the contributors will be added to the reference section in this post
Q1: Which of the following three is the strongest password?
- starwars
- 1qaz2wsx
- trEEGCv-
Q2: Which of the following is a weak password?
- 123456
- P@ssw0rd
- ILoveYou123
- All of the above
Q3: How often should I change a password?
- Never
- Every week
- Every month
- Every year
- Only when there's proof or suspicion of compromise
Q4: Is it considered safe to use the same complex password on all websites?
- Yes
- No
Q5: What should I do after I learn about a data breach of a website? Choose the best answer.
- Nothing
- Change the password of my account for that website
- Change the password for my account for that website and of all other websites where I use that same password
Q6: What are the characteristics of a strong password?
- Long
- Long, random and unique
- Long, unique
- Long, random
Q7: If you want to share a password with someone, what's the best option?
- Send it via email
- Send a text message
- Tell it via the phone
- None of the above
Q8: Which of the following is the most secure backup strategy?
- One backup on an external harddisk and another one on a cloud backup
- 2 backups on 2 different external harddisks
- A backup on an external harddisk
Q9: You open a website and it has a padlock in the browser bar (the lock icon in front of the URL). Which statements are true?
- I can be sure that this is a legit, non-malicious site
- It tells me that the site is 100% secure
- The traffic between my computer (browser) and the server that runs the website is secured
- No one, even my Internet Service Provider doesn't know which site I visit.
- This could be a phishing site.
Q10: Is it generally considered safe to use Starbucks Public Wi-Fi network for performing an online banking operation?
- Yes, it is safe
- No, it is dangerous
Q11: Is it secure to enter your private information (e.g., data of birth, identification number etc.) on a site that starts with "http://"?
- Yes
- No
Q12: Which of the following statements are correct? When I use incognito or private mode in a browser...
- No one can see the websites I visited, even not my Internet Service Provider.
- Others that use my device can't see which sites I visited
- I'm anonymous for that website
Q13: Your business email account has been compromised and leaked in a data breach. What is the best course of action(s)?
- Change your password immediately
- Inform the security team of your organization
- Change the Password on all sites where you use the same password
- All of above
Q14: Is it useful to run antivirus software on an Android phone?
- Yes
- It depends, only if you download apps from outside of Google's official app store
- No
Q15: Which of the following are considered personal data under GDPR (more than 1 answer possible)?
- Your IP address
- Your birthdate
- Your home address
- Only your firstname
Q16: If you receive a call from someone that says to be a clerk from your bank, is it ok to give your bank account details over the phone?
- Yes
- Never
- Only if I recognize that the phone number is from my bank
Q17: You receive an email with subject: "$5 million donation from Bill Gates" and in the email they ask you to provide your telephone number and full postal address to claim the money. What's the best action?
- Reply with my phone number and postal address, I want the 5 million dollars
- Forward the email to friends, because sharing is caring
- Report the email as spam and delete it
Q18: You're browsing and on a random site a pop-up to get free access to Netflix appears. What's the most secure action?
- Follow the pop-up instructions to get the free access
- Immediately close the pop-up and don’t proceed
Q19: You receive an email from '[email protected]' that urges you to reset your Hyundai password. What should you do?
- Change my password immediately as per the instructions given in the email
- Don't proceed and delete the email
Q20: Is the following statement true or false? Reusing the same password across multiple sites is a good idea. It's very convenient after all.
- True
- False
Q21: Is it considered a good security practice to leave your machine unlocked when you leave your desk?
- Yes
- No
Q22: If you receive an unexpected phone call from Microsoft technical support, should you?
- Follow their instructions
- Give them your password
- Call them back
- Hang up
Q23: If you receive a suspicious email, should you?
- Reply to it
- Open the attachments
- Click the links
- Report it to the phishing reporting mailbox of your government
Q24: You’re being texted that your parcel delivery will be delayed. In order to expedite it you need to?
- Reply to the text
- Click on the link provided in the sms
- Think first. Am I expecting anything? If not report and delete the sms
Q25: Is the following statement true or false. Because operating system updates are time consuming and may need to restart the machine it's a good idea to postpone them as long as possible.
- Yes
- No
Q26: Which of the following statements are correct?
- Phishing is a form of social engineering.
- Phishing is a so called "spray and pray" technique in which an attacker sends out the same email to hundreds of potential targets in the hope they will fall victim.
- All of the above
Q27: Imagine you work for the finance department of a company. You received an email from your company’s CEO and they want you to immediately transfer a few millions to a bank account provided in the email. Will you execute the transaction?
- Yes, I will do so if my CEO asks me.
- I will only execute the transaction after I got confirmation from the CEO through another channel.
Q28: If you suddenly see the following page in the browser, is it a good idea to claim your present?
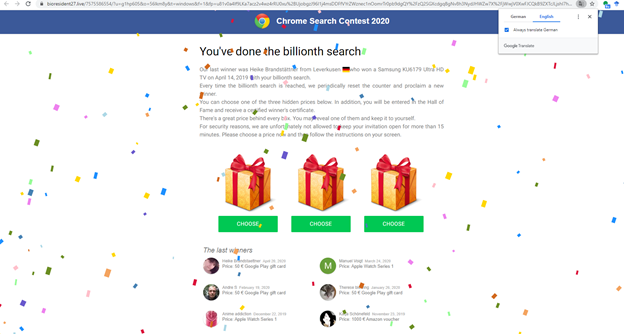
- Yes
- No
Q29: Which of the following statements about a phishing email are true?
- The email comes out of the blue. There's no context or previous contact with the sender
- The email contains a sense of urgency to get a particular action done
- All of the above
Q30: You receive a SMS from a supplier/vendor who asks you to click on a link to renew your contract. You should:
- Proceed without worrying
- Don’t proceed by clicking on the link in SMS
Q31: Which month is considered or recognized as Cyber Security Month?
- September
- October
- November
- December
Q32: The person who performs a social engineering attack is known as?
- An Information Engineer
- A Social Engineer
- A Social Media Activist
Q33: Imagine you find a USB device in the hallway at work. What's the best thing to do?
- Pick it up and plug it in to see what’s on the USB device. Maybe you can identify the owner.
- Leave it in the hallway or bring it to the reception desk, such that the person who lost it can get it back.
- Pick it up, don't plug it in but inform your IT department because this could be a USB device containing malware to infect your company's systems.
Q34: Which URL(s) bring(s) you to Google’s Home Page?
Q35: Which of the following URLs could NOT be used in a so called 'Typosquatting Attack'?
- http://microsoft.com
- http://mircosoft.com
- http://miroosoft.com
- All of the above
Q36: You receive the following email which contains "This message was sent from a trusted sender" in the body. Does this mean you can trust that this email is legitimate?
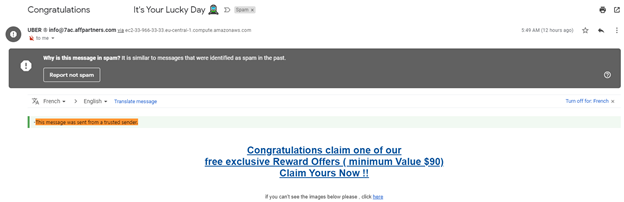
- Yes
- No
Q37: If you receive the following email, is it a good idea to proceed to get help from CBD?
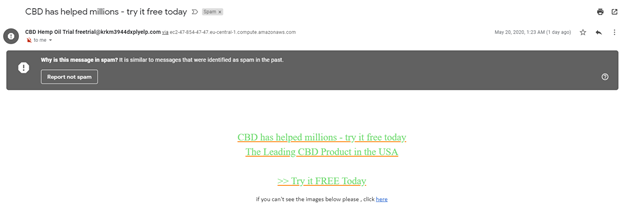
- Yes
- No
Q38: You receive the following invite to take a quiz. You decide to take the quiz to receive the free glasses. This is...
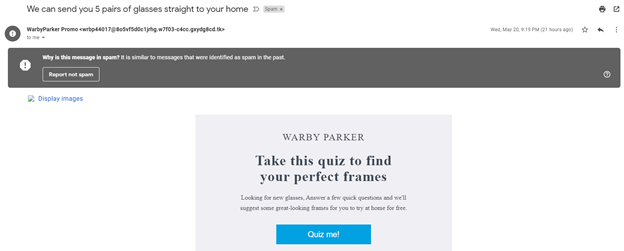
- A good idea, free stuff is always nice
- This is a bad idea, this is a scam to steal my personal data
Q39: Which of the following things help to decide whether an online shopping website is trustworthy?
- The address of the website starts with 'https://'
- There's a seal on the website that says '100% secure'
- Do a bit of research to see whether the site has a good reputation
- Read on the website and look for positive reviews of other customers
Q40: For online shopping it's best to use...?
- A credit card
- A debit card
Q41: I don’t use a PIN on my smartphone but keep it with me. What could go wrong?
- When I lose it all my information and apps are accessible by the finder.
- When I leave my phone unattended, miscreants can gain access to all my online accounts using my email address.
- When my phone gets stolen the thieves can access all my information and apps.
- All of the above.
Q42: Is it a good idea to pay criminals that encrypted the files on your computer by deploying so called ransomware? Why or why not? Select all applicable answers.
- Yes, because you can be sure you will regain access to your files.
- Yes, because you don't have to care about backups yourself.
- No, because you have no guarantee that you will regain access to your files.
- No, because even when you get your files back criminals might attack you later again because they are still active on your network.
The answers to these questions can be found here
Contributors
A big thank you to the following people for contributing:




