Maybe you heard about password cracking, but you don't know what it's all about and which risks it poses for you? Then this article is for you. It will help you to understand at a very high level what password cracking is and foremost what can you do to protect your passwords as much as possible against it.
Let's start with the bad news, you have no influence on how a particular website or app stores your password. You rarely know how they secure your passwords, if they do it at all.
If a website stores passwords in an insecure manner your password can be quite easily retrieved when they get hacked.
It could be that the passwords are in readable or reversible format (encrypted) in the database or they can be hashed with an algorithm that's no longer considered secure.*
In the former case it's trivial, but also in the latter case your passwords are at risk because they can be cracked. And even with secure algorithms, when your passwords are not strong enough they still can be cracked.
*If you want to learn more on how passwords should be stored securely, read this blog.
What is password cracking
It's actually the hash, a scrambled representation of your password, that possibly can be cracked.
Hashing is an irreversible algorithm, that's why there's no such thing as dehashing.
And this is where cracking comes into play. Let's say a website implements the bcrypt hashing algorithm and the database gets hacked. One of the password hashes looks like this:
$2y$10$/3APyPj0wgOIP8KPORuFseguqahtL0IuoHPqebeXTIu5mqhENWkK.
I'll use this particular hash an example to explain, in a very simplified way, what cracking a password hash means. The same hashing algorithm used by the company from which the data is leaked, is used to calculate hashes from text input until the calculated hash matches the leaked hash. When this is the case you know the plain text password that corresponds with the hash. This process is not done for one hash but for entire lists of stolen or leaked hashes.
You might think this is not very effective, but researchers and unfortunately also criminals use giant rigs of processors - mostly graphical cards - to compute billions of hashes per second. Like the below tweet shows, the number of hashes that can be computed depends on the type of graphical cards and the hashing algorithms that are used.
Ever wondered what a #hashstack @hashcat cluster of 448x RTX 2080s could do for #cracking #passwords using the full US keyboard? https://t.co/NKYIrKwUDb pic.twitter.com/a1ML01ZM2Q
— Terahash (@TerahashCorp) July 27, 2019
Your best defense against password cracking
I mentioned that when your passwords are not strong enough they can be cracked.
But what makes a password a strong one? A good password must be sufficiently long, random and unique. If you want more details on what this means I suggest you to read this blog post.
A strong password might look something like this for instance.
JM.2^Y7JPP]AKjn8ms}WJbb=XsZ?@NDg
This 32 character long password is truly random. Such password is with current cracking capabilities virtually impossible to crack, but who knows, it could be possible in the future due to the increase in computing power.
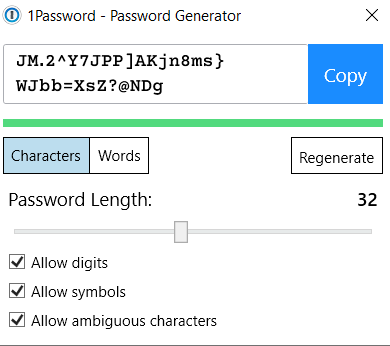
I use a password manager for generating these kind of passwords so nothing prevents me from creating even longer passwords. Unless a particular website doesn't allow this, which is unfortunately still the case sometimes.
While this password can't be (easily) cracked (at the moment), it's important that you use a unique and thus different password for each online service. Like said earlier you have no control about how a website or app stores your password. If it doesn't store your strong password with a secure hashing algorithm and you reuse it for another account attackers might still gain access to that other account!