This is the second post in the Secure Password management series. Read the previous one here.
What's an appropriate minimum password length? When I asked this question on Twitter a while ago most people voted for 14 or higher.
I'm having an interesting chat with @wimzkl. I think the topic is worth turning into a poll. What's a good minimum length for passwords? Please also motivate your choice. #Password #Security #UX
— John Opdenakker (@j_opdenakker) April 17, 2019
To be clear, the question here was about the minimum password length authentication systems should require.
However it is not in scope of this post, my advice to end users on minimum password length is simple. Make your passwords as long as you're able to manage within the constraints of the authentication system. More info about how to do this is for an upcoming blog post in this series.
The longer, the better?
So almost half of the voters would require passwords to be at least 14 characters long. Several people recommend to use real long passwords, 24+ characters.
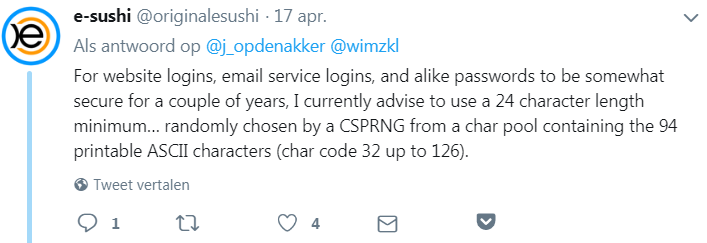
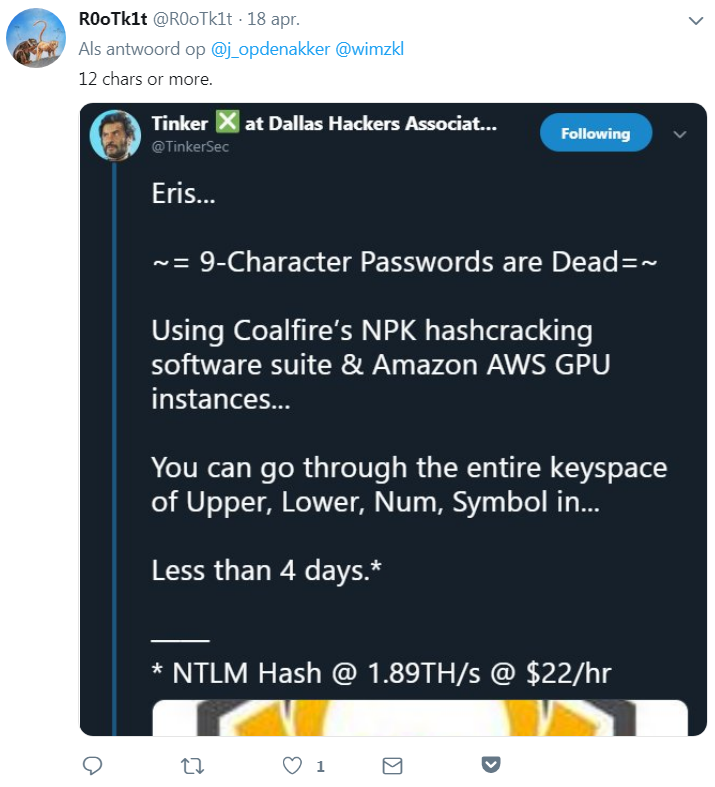
Another person said at least 12 characters long, explicitly referring to current hash cracking capabilities.
What are we defending against?
To build secure password based authentication systems it's important to understand the different kind of password attacks.
We must distinguish between offline password attacks, where there’s no interaction with the system under attack and online attacks, executed directly against the system under attack.
In offline password attacks, attackers try to crack password hashes on their own (or nowadays often cloud) infrastructure and use these cracked passwords to gain access to user accounts. This gives them an enormous advantage, they can spend as much time as they want to crack the hashes. The best possible defense we have is slowing them down. And this is typically done by using a slow hashing algorithm that’s adaptable over time.
But even if you use bcrypt, like Cloudpets did, when you don't force a minimum password length at all, attackers will crack a lot of passwords. So we need to enforce a minimum password length that is large enough. I'll come back to what large enough is - in my opinion - later in this post.
Also note that uniqueness of a password is very important to defend against offline attacks.
There are many different kind of online password attacks. For instance credential stuffing attacks, brute force or password guessing attacks or password stealing via man-in-the-middle attacks, phishing or malware. They all require different kinds of security controls, none of them have anything to do with password length though.
Blocking brute force attacks is very hard and must be implemented with care.
Protecting your users against credential stuffing attacks, which only exist because a lot of people reuse passwords, isn't straightforward either. Blocking the most frequently breached passwords - this also is helpful against brute force attacks by the way - and checking the location from which a user logs in, are a few of the security measures that might help. 2FA is still one of the most effective security measures, but as it still poses a usability barrier we don't see companies enforcing it upon their users.
Make it secure but usable
In the previous section we've seen that it's important to have a layered defense to protect password based authentication systems. And like Daniel Card says, there's no one-size-fits-all solution.
Okay, it's clear by now that length is important, so why wouldn't we indeed require users to create passwords with minimum length 24?
Well, there's the usability angle. Can you imagine that you're non-tech and non-security savvy friends and relatives have to come up with such long passwords? And not only that they should use a different one for every (online service). This is just not feasible.
But we could solve that with passphrases, right?
If you have only 5 or 10 online accounts, for which you're not required to change your password every few months, this might work. But this is the exception rather than the rule.
Furthermore, account registration should be a straightforward and flawless experience, at least if you want to have people using your service.
Conclusion
When it comes to password length, longer isn't necessarily better. Long passwords that are previously breached or contain repetitive patterns are not secure at all. That's why we need to prevent users from choosing such weak passwords.
Enforcing a minimum password length is crucial. But when it's set too high, for the majority of users - that don't use a password manager - choosing a password will be a hell of a job.
It's all about finding the sweet spot between security and usability. I'd say a minimum length of 10 should be sufficient, at least when combined with additional offline and online password attack defenses like described earlier.




