This is the third post in the Secure Password management series. Read the previous ones here and here.
This is an extract from research that Microsoft published in June 2016.
For Microsoft account, we see hackers testing leaked credentials against our systems at an average of 12M credential pairs every day
This kind of attack is called credential stuffing. According to wikipedia:
Credential stuffing is a type of cyber attack where stolen account credentials typically consisting of lists of usernames and/or email addresses and the corresponding passwords (often from a data breach) are used to gain unauthorized access to user accounts through large-scale automated login requests directed against a web application
Given the prevalence and size of these attacks and the fact that users keep on (re)using weak passwords and the same username (often their email address) for their online accounts, this is not an easy problem to solve. And after all, who's responsible to successfully defend against credential stuffing attacks? I did the following poll on Twitter.
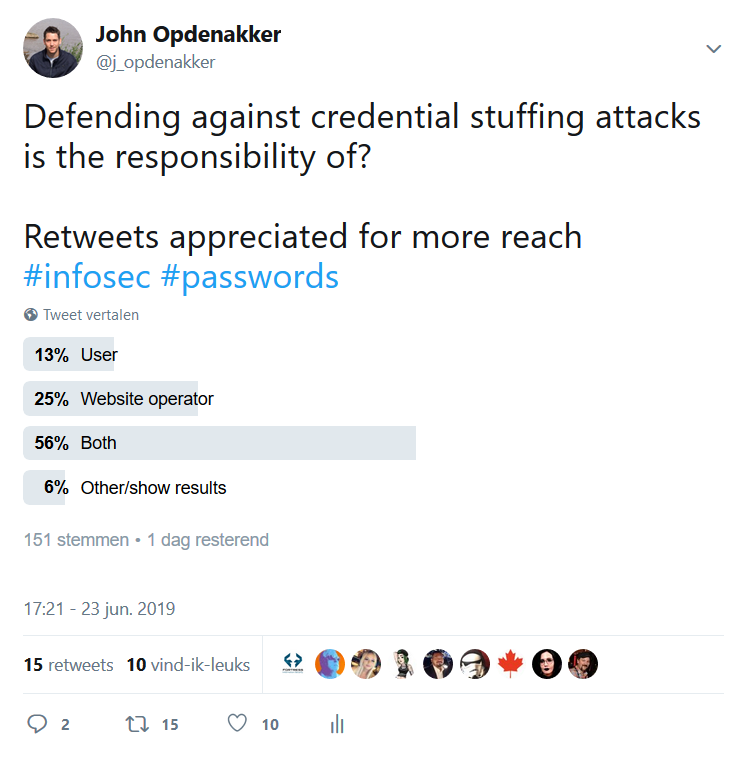
The poll is still running, but the trend is quite clear. Most people say that the responsibility lies with both the user and the website operator.
And I tend to agree with the majority here. While we could say in theory that the user is responsible for choosing a unique combination of username and password, it's a fact that still not many people do so.
This was proven in a survey Google did earlier this year in partnership with Harris Poll. They questioned 3,000 adults (ages 16–50+) living in the U.S. to understand their beliefs and behaviors around online security. The diagram below shows that only 35% use unique passwords for every account.
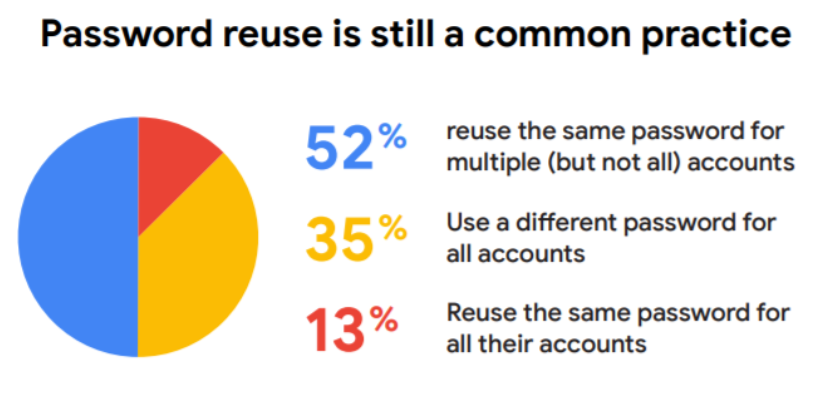
There is still a lot of improvement possible via user awareness training, but with awareness only we will not stop these attacks.
Website operators should be aware of this and protect the users.
What you can do as a user
There are some measures you can take as a user to protect yourself against credential stuffing attacks:
- Use unique passwords for every online account.
- Use a unique email address for the most important online accounts (e.g., financial accounts, social media accounts)
- Use an email alias for every online account (e.g., myusername+twitter@gmail)
- Activate two-factor authentication
What you can do as website operator
Detecting credential stuffing attacks might be not as easy as it seems at first sight.
If you deal with a naive attacker who uses the same IP address to try thousands of credential pairs against your service, one after another, it is quite easy to detect. You can monitor for this kind of abnormal behavior and block the IP.
But things change when an attacker has a botnet with 1million different IPs at his disposal, and instead of firing each username/password pair one after another, plays with the timing to bypass implemented detection measures.
There's maximum 1 - failed or successful - login from each IP. So blocking the particular IP address is no option here because you might lock out legitimate users. That's why you should certainly monitor for logins from unknown devices. A user that normally logs in from Belgium that suddenly logs in from Russia is abnormal behavior. Whenever you detect such a potentially suspicious login attempt notify the user immediately so he can take action.
But this still implies that the attacker can have accessed your account and potentially has locked you out of it.
The most effective protection against this is Multi Factor Authentication (MFA). For user accounts that have MFA enabled you can request the verification code for each login from an unknown device.
The problem is that it's really hard to force users to enable MFA because there's still a usability barrier for a lot of people. So for users that don't have MFA enabled you could show a captcha at potentially malicious logins. Keep in mind though that captcha have a negative impact on usability and are not impossible to bypass.
Other security measures that should be part of your defense in depth strategy:
- Avoid email addresses for username
- Prevent users from using known breached username/password pairs. You could use for instance Troy Hunt's APIs to implement this.
- Scan your existing user base for use of known credentials from a new data breach and reset impacted users' passwords.
The latter is exactly what TripAdvisor did the other day to protect their users.
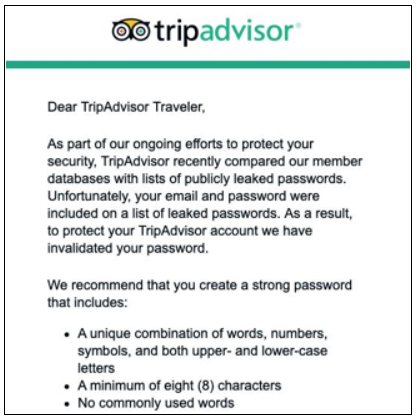
When you reset the passwords of your users make sure that you clearly communicate why to avoid speculation. I think TripAdvisor have done a great job both resetting the password and the communication they have sent to their users.
Conclusion
Creating awareness about secure password usage only helps to a certain extent. The real key to success is detection and mitigation where the attacks happen, on the web applications. As a website operator, guide your users in creating strong passwords and detect and reset when they're using weak ones. Both your users and you will benefit from it.

