This is my first blog in a series of daily security blogs I plan to publish in October. With these blogs I hope to reach not only my typical audience, security professionals, but especially less security aware people. If you think the content is helpful for people you know, share it with them!
My goal is to make more people aware of the risks inherent in using the internet and everything connected with it. And of course provide people with actionable tips to improve their online security.
With this intro post I would like to set the scene why online security matters for everyone.
Understand what's at stake
Whenever you register an account for applications like Facebook, Instagram or Gmail you have to provide personal data before you can even start using the application.
This data is then stored on Facebook's computer systems. But unfortunately it's not limited to the data you enter at registration. Facebook follows everything you do on Facebook and even outside of it. I encourage you to read this article to get a better understanding about what they know and which kind of data about you they collect and store.
It doesn't stop there. They share your data with many other companies. I think most people heard about the Cambridge Analytica scandal. Cambridge Analytica is a data mining company that improperly obtained access to 15 million Facebook user profiles. If you're interested to know more about it, watch this video.
Another example of a company that massively shares and sells your data is PayPal. The image below shows only a fraction of the third parties PayPal shares your data with.
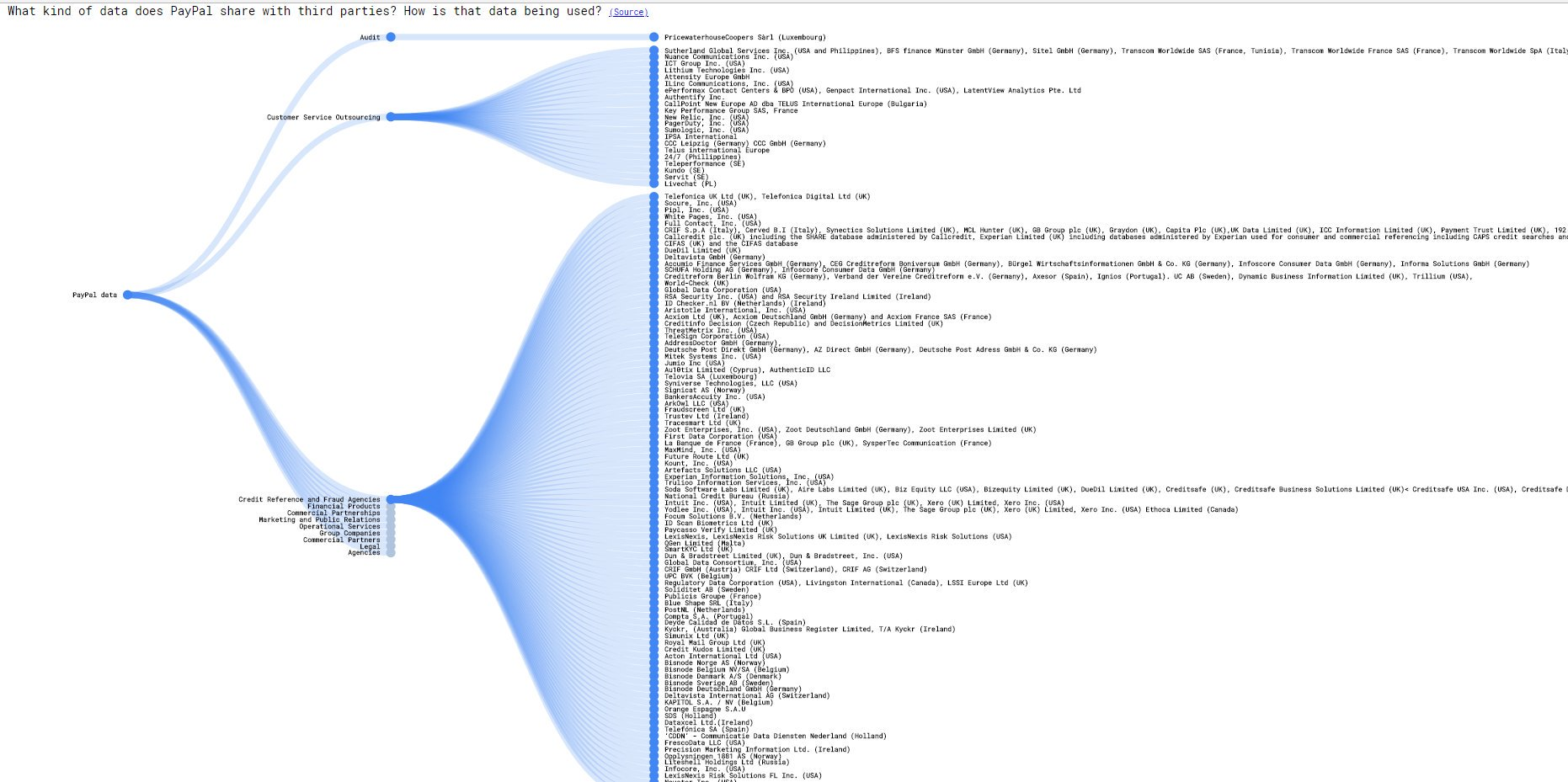
So the data you provided can now potentially be stolen from the PayPal servers, plus from all these other companies.
But unfortunately it's not limited to that. Let's go back to the example of Facebook. The mobile Facebook apps on your phone and tablet also have access to your facebook data. This means that whenever an attacker gains access to your mobile devices he can do whatever he wants with your Facebook account. And that might be the least of your worries because the attacker now has access to everything on your phone. And at that very moment he can do virtually everything you can do online. He can impersonate you.
Another example are email accounts. Email accounts are your most valuable digital assets because they contain a lot of personal data and you use them to register for other online accounts. Once attackers have access to your email account they can change the password and lock you out of your own account. Even worse they can issue password resets or recovery for applications for which you registered with that email address and take over these accounts as well.
And we don't always have to think about malice. What if your phone no longer works and the pictures of your family are not properly backuped? Again you lose precious data.
Another big security risk are internet connected devices. They often use default passwords and have other serious security risks. This can for instance lead to situations like this where internet connected baby monitors get hacked.

There are much more examples about what can go wrong, but I'm gonna stop here for now. I get that this can sound frightening for a lot of people, but it's the unfortunate reality we have to deal with. The good news is that we can take security measures to limit the risks we face. And like I said the aim of this blog series is to help you with that.
But this won't happen to me, right?
From personal experiences I know that many people think they are not at risk because they are not an interesting enough target for attackers. Nothing is less true.
Think for instance about phishing mails or text messages in which criminals try to lure people to hand over confidential data like their username, password or credit card data via links leading to fraudulent websites under their control. Criminals send these malicious mails to massive lists of email adresses or phone numbers, which they can easily obtain on the internet.
Selling stolen data is a very lucrative business for criminals. There is an underground economy on the internet, often refered to as the dark web, where all kinds of stolen goods (not only data) are heavily traded.
A look inside Dark Web:
— Bank Security (@Bank_Security) September 30, 2019
- Stole Credit Cards & Skimmers
- Bank Credentials
- Cloned ATM Cards, Credit Cards & Skimmer Aplenty
- Money Schemes & Money Muleshttps://t.co/cEODExUE3J pic.twitter.com/NjAMK94l7Z
The data traded there are certainly not only gathered via phishing attacks. The most common way people's data get stolen is because companies that store their data get hacked. These data breaches result in billions of data records being exposed.
Another common practice from criminals is trying of authenticate with stolen username and password pairs against online services. This is done in an automated way. Microsoft research from 2016 showed that on average 12 million leaked username and password pairs were tested against their systems.
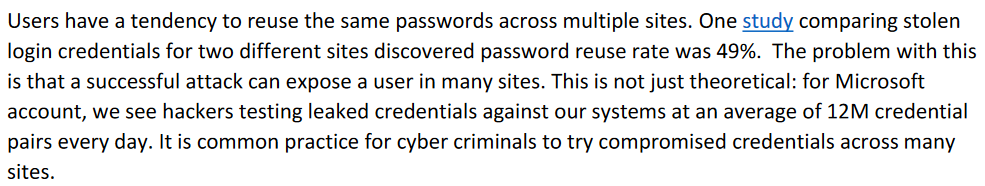
Whether they try to steal the data from you directly or from a company that has your data, the criminals' goal is often to monetize people's data in one way or the other.
Extortion is another frequently used technique criminals use for financial gain. Ransomware, malware that locks electronic files on your computer and mobile devices, is the most well known. But recently people get more and more of these mails, which are refered to as sextortion mails.
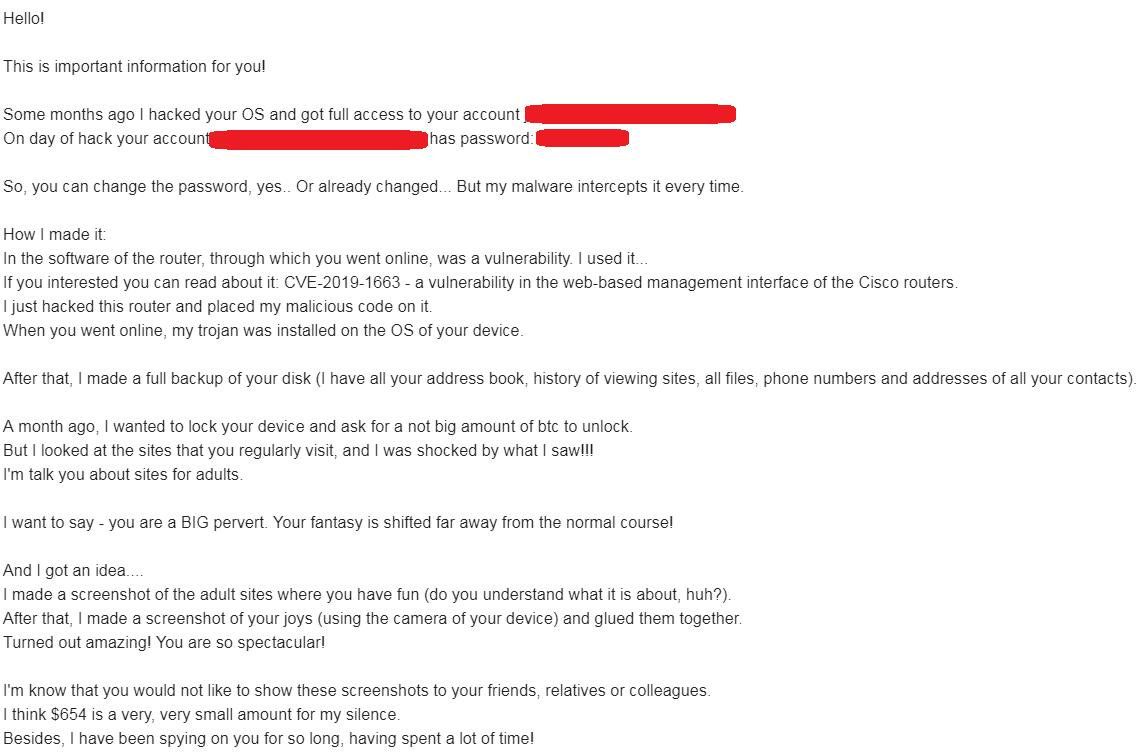
The approach is simple, yet very clever. On top of the usual threats of leaking compromising information they claim to have about you, the criminals use leaked passwords associated with your email address to give extra credibility to their claims.
And sad but true, there always will be perverts that are after sexual oriented content.
Former Yahoo engineer pleads guilty to hacking user emails in search for porn
— Catalin Cimpanu (@campuscodi) October 1, 2019
-worked as Yahoo! Mail site reliability engineer
-broke into 6k Yahoo inboxes
-most belonged to young women
-also reset passwords and broke into FB, iCloud, Dropbox accountshttps://t.co/EhkhE8ek1B pic.twitter.com/n2j2tVavXI
Be prepared
I want to conclude with this story about Mat Honan who's entire digital life was destroyed. This story illustrates a few key points about security incidents:
- It can happen to anyone.
- The impact can be devastating.
- It potentially could have been prevented with the right security measures.
If you don't read the story I want you to remember the following parts.
There was no particular reason that the criminals attacked him:
"I asked Phobia why he did this to me. His answer wasn’t satisfying. He says he likes to publicize security exploits, so companies will fix them. He says it's the same reason he told me how it was done. He claims his partner in the attack was the person who wiped my MacBook."
The impact was devastating:
"In the space of one hour, my entire digital life was destroyed. First my Google account was taken over, then deleted. Next my Twitter account was compromised, and used as a platform to broadcast racist and homophobic messages. And worst of all, my AppleID account was broken into, and my hackers used it to remotely erase all of the data on my iPhone, iPad, and MacBook."
Unfortunately he had no backups of his files:
"Had I been regularly backing up the data on my MacBook, I wouldn't have had to worry about losing more than a year’s worth of photos, covering the entire lifespan of my daughter, or documents and e-mails that I had stored in no other location. Those security lapses are my fault, and I deeply, deeply regret them."
Don't let the kind of incidents I've discussed throughout this post wipe out (parts of) your digital life or result in financial losses. Anticipate and be prepared. I hope you follow me along my journey to help you become more secure online. Stay tuned for more tomorrow!




