Most people have a lot of internet connected devices at home. Obviously computers, laptops, tablets and smartphones, but it doesn't stop there. TVs, dishwashers, kettles, wearables, toys and even toilets all have smart, internet connected models nowadays.
Connecting all these devices to the internet and to each other is what's referred to as the Internet of Things (I0T).
The big problem is that most of these IoT devices are poorly secured and therefore introduce a lot of security risks.
Default, weak or no passwords at all.
End 2016 a security researcher plugged a Wi-Fi-connected security camera into his network. It took only 98 seconds after it was infected with malware.
But how could this happen so fast?
Because this particular camera used a default password. The malware used a list of known username and password combinations to try to gain access to the camera.
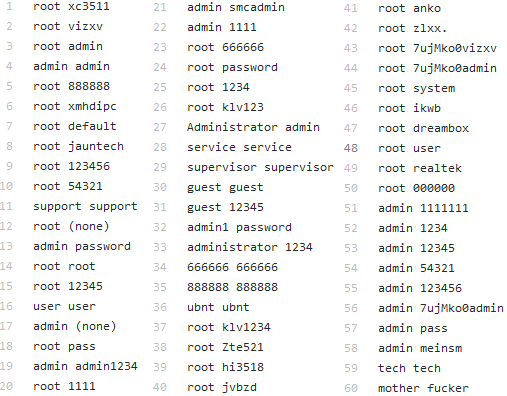
The purpose of this malware is to infect as much devices as possible to make them part of a botnet. A botnet is a network of private computers infected with malicious software and controlled as a group without the owners' knowledge. These botnets can for instance be used to spread spam or bring down other websites via so called Distributed Denial of Service attacks.
Almost no one changes the default passwords of their webcam or any other IoT device, that's why these malware attacks are so succesful. And let's be fair, many tech-savvy people would not succeed in getting the password changed before the device is infected.
Some IoT devices even don't use a password at all. This is an example of a webcam somewhere in a living room in Argentina which is accessible over the internet and can be easily found by Internet of Things search engines like shodan.

Vulnerabilities and hacks
A lot of IoT devices have severe vulnerabilities. A really scary example is for instance the TicTocTrack watch, a smart watch to track your children. I really recommend you to read this research blog. It's important that you understand both the privacy and security risks of these tracking devices.
In any case do watch this video:
One of the security researchers was able to add himself as a parent to the TicTocTrack watch of the other researcher's daughter. And that means he could do the following:
"A parent can call the device and have it automatically answer without interaction by the child. The watch actually says "Dad" next to a little image of a male avatar so a kid would think it was their father calling them".
Another stunning example of the risks of IoT devices is this one. A casino got hacked through an internet connected thermometer in their fish tank.
"the hackers exploited a vulnerability in the thermostat to get a foothold in the network. Once there, they managed to access the high-roller database of gamblers and "then pulled it back across the network, out the thermostat, and up to the cloud."
And a last example is this internet connected baby monitor that got hacked.

The updating problem
Yesterday I explained why it's important to keep your software up to date. That's no different with IoT devices. I hope by now it's clear that it's important to apply firmware and software updates.
The problem is that a lot of IoT vendors don't foresee regular (security) updates. A recent example is D-Link that doesn't patch a critical vulnerability.
For most IoT devices it's also not trivial to install updates like it is for instance on Windows or iOS systems. Another big problem is that it's mostly unclear how long the support period is. What if your smart TV is 3 or 5 years old and it doesn't receive updates anymore?
IoT security recommendiations
My single best security advice is not to buy IoT devices. But if you really want to, here are some tips.
- Do some research upfront. Only buy IoT devices if you can change the password for the device. You must know whether it has a default or a unique password. If it has a default password you must change that straight away when you install the device. Make sure regular updates are available and the device is supported (with updates) long enough.
- Isolate your IoT devices in a separate network, such that when they are hacked the attackers can't gain access to your internal network.
- Change default passwords immediately.
- Regularly install updates, both firmware and software.
Conclusion
Next time you want to buy an IoT device think twice. Unfortunately securing IoT devices is very difficult, sometimes even impossible. Ask yourself if you really need that particular smart device? Probably not.
If you want to buy an IoT device, do some research upfront and make sure you secure the device properly when you install it and keep the device updated. When you're not able to secure it properly, just don't buy it.
That's all for today. Tomorrow will be the last post of my October security awareness blog series.




