I’m overly paranoid about every unsolicited communication. Whilst a lot of friends and colleagues probably think I’m crazy, a healthy dose of caution largely reduces your risk of being compromised. In this post I’d like to give a few practical guidelines that can save you from a lot of trouble.
Consider every link, attachment or file to be suspicious
Whenever you receive a link via email, chat or SMS consider it potentially dangerous. The best advice is to never click links but instead browse to the respective websites.
For several reasons it’s a good idea to use a password manager, but what many people don’t realize is that a password manager can also help to stop phishing attacks. Let’s say you click on a Dropbox password reset phishing link because you think it’s a legitimate link issued by Dropbox. When you notice that your password manager doesn’t recognize the URL, that should alert you that you’re on a phishing site.

Be very careful with downloading email attachments or files sent via chat. Even when they come from a known email address or from one of your chat contacts, this doesn’t guarantee that you can trust them to be safe. Emails can be spoofed, email or chat accounts can be hacked and sim cards can be swapped. In case of doubt, verify via another channel if the particular content was really sent by the expected person.
I also extensively use tools like Virustotal and urlscan.io to scan files and links on malicious content.
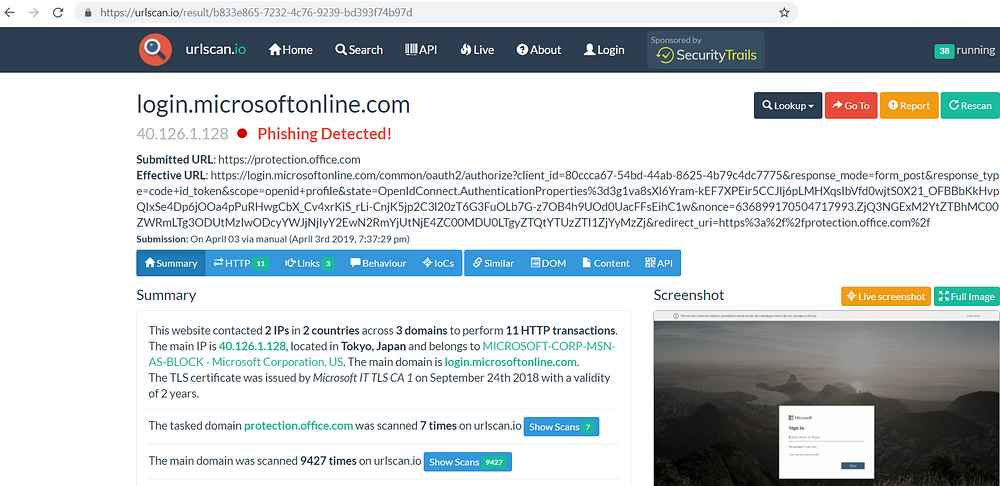
Consider every online service to be hacked
Even if a website or application isn’t (yet) known to be hacked, consider it as such. By doing so consistently you will make the best possible choices to protect your accounts. A a minimum you should use:
- A unique password for every application
- Two-factor authentication whenever available
- Account recovery options

Consider all your personal data to be publicly known
Most of your personal data are spread all over the internet. It’s an inconvenient truth, but when you keep this in mind you can protect yourself a bit better.
A lot of people falsely conclude that a message containing personal information and/or coming from a known sender must be legit. But your personal data can be assembled from one or more data breaches and as we have seen the sender can be spoofed or accounts can be hacked.
The best known example is phishing. Certainly targeted phishing mails, so called spear phishing, are very effective because both the sender and the information in the mail look trustworthy to the receiver. This is how huge amounts of money get stolen from companies. For instance, the criminals spoof or hack the email account of a manager and request an employee to transfer a large amount their bank account. This is an actual threat and companies should have very rigid procedures in place to prevent this from happening.
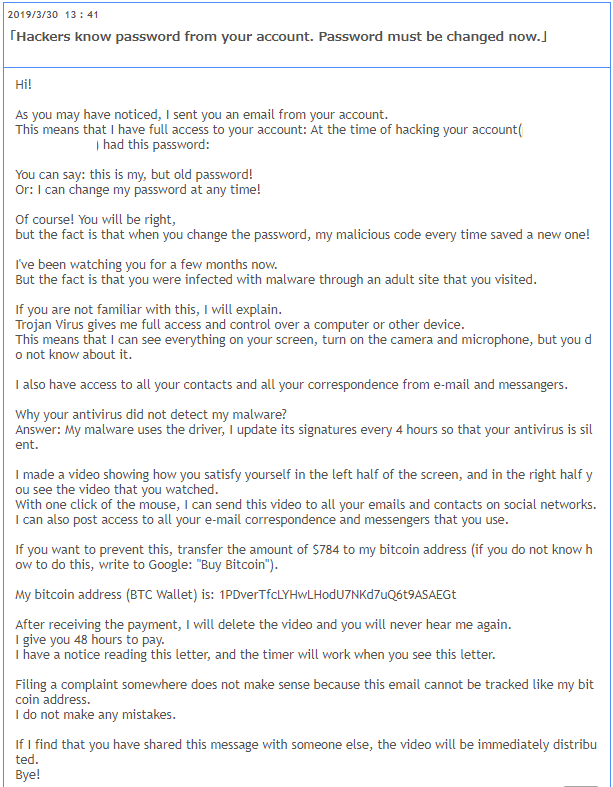
Another phenomenon on the rise recently is (s)extortion. Criminals use stolen data — in this case email credentials — in attempts to extort people. Like the phishing attacks, these scams are also based on publicly available data and the fact that email accounts can be spoofed.
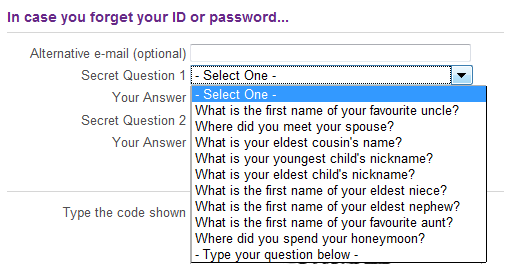
One last example I’ll give are security questions. You can configure them for instance for account recovery purposes. When an attacker can get the answers to these question right he can gain access to your account. A lot of these questions have either predictable answers or the answers can be easily found via Open-source intelligence (OSINT). That’s why you should try to avoid this type of questions or when this is not possible give fake answers.
Conclusion
As a general advice. Be cautious, even when the person communicating with you appears to be someone you know. Consider everything to be hacked and your data to be leaked. With this approach you will notice that you’ll take thoughtful decisions and improve your security.

