If you’re not yet monitoring your data breach exposure, I really recommend you start doing it now. If you’re already doing it, I hope this post is still useful as I’ll share some tools and best practices with you.
Why?
When your credentials of an account are compromised, the first thing you need to do is change your password. And hopefully only for that particular account. You know that password reuse is BAD, right?
But how do you know if they got breached in the first place? Best case scenario is the hacked company is aware of the data breach and informs the impacted users. But there are a lot of cases where the data is already circulating on the internet and the company doesn’t even know (or reported) they suffered a breach.
And this is were data breach monitoring tools can help.
Data breach monitoring tools
Have I Been Pwned
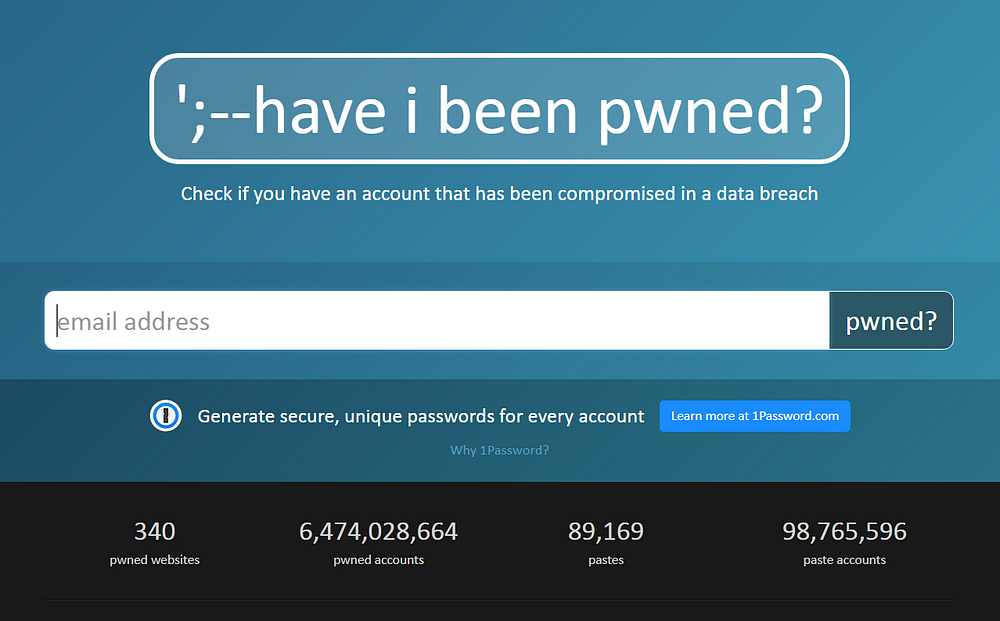
The first one is probably the most widely known. “Have I Been Pwned” is a data breach notification service by Troy Hunt. You can just search on email address to see in which data breaches it was found, but more powerful is to subscribe to the notification service. Do this for all your email addresses. Whenever a breach is loaded into Have I Been Pwned and a subscribed email address is found in it, the owner will receive an email notification.
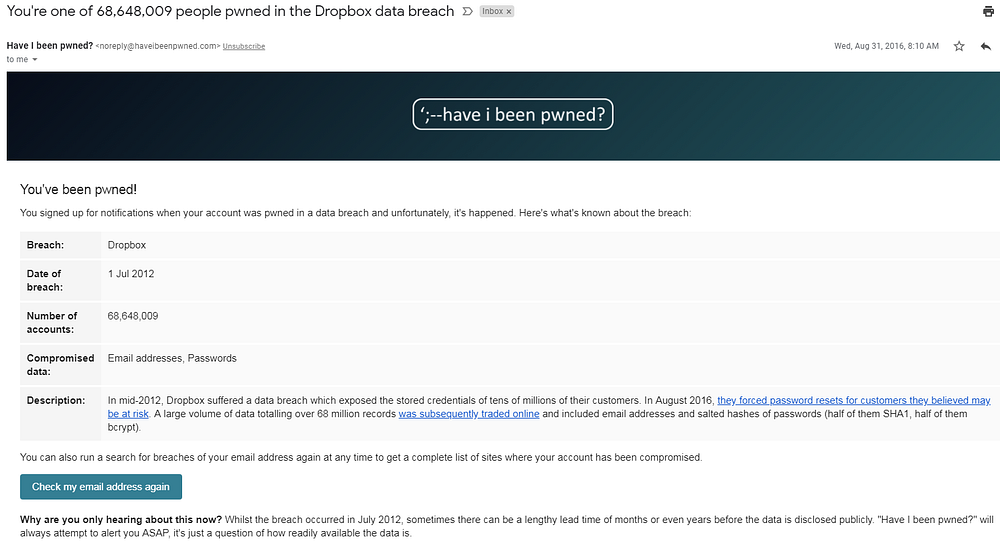
Have I Been Pwned has also a domain search feature which is particularly interesting to companies to find all email addresses on their domains that have been found in any of the data breaches in Have I Been Pwned.
Note that Troy Hunt is not actively monitoring for data breaches, he adds only breaches that he get’s sent by people.
Hack Notice
And that brings me to HackNotice. This service uses a bit different approach. First of all they are actively looking for data breaches.
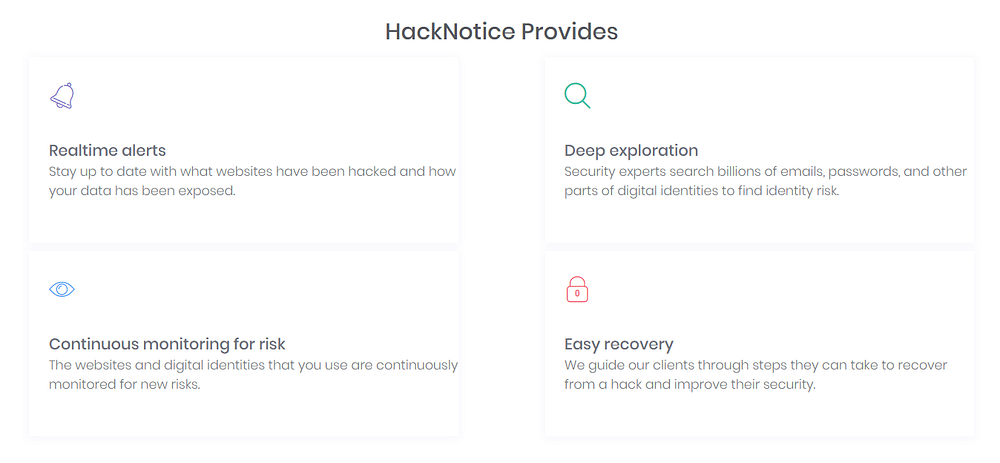
You can define domains, apps or company names to monitor for hacks in what they call the “Hack Watchlist”.
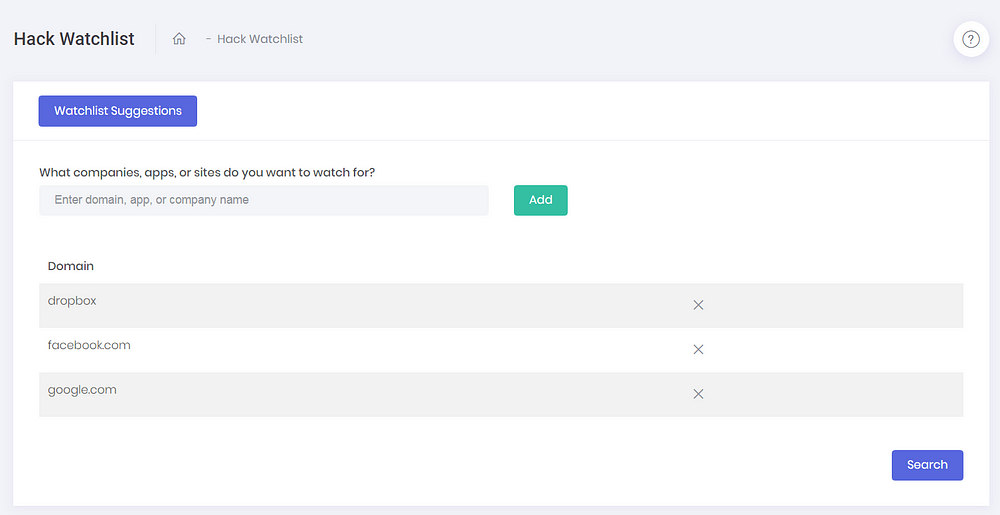
You can also define for which identities you want to be alerted if they’re involved in the hacks you defined in the “Hack Watchlist”
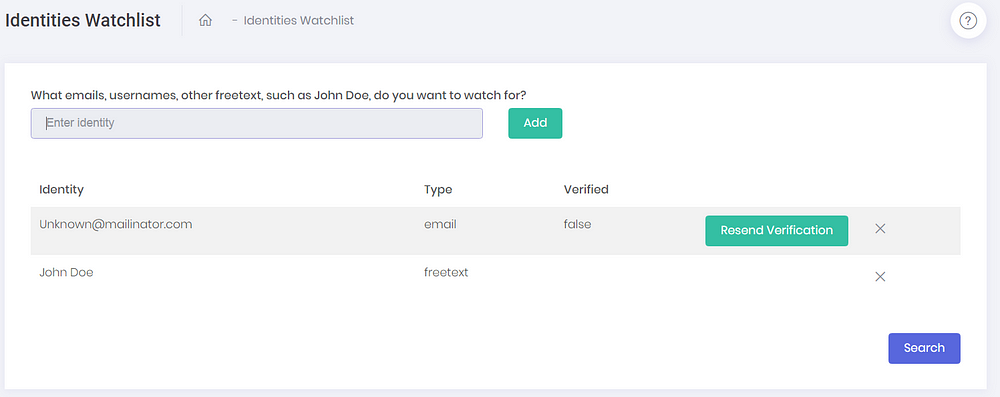
If a match is found you’ll be notified via email.
HackNotice does also provide domain monitoring and some other services for businesses
Identity leak checker
The identity leak checker made by the Hasso-Plattner-Institut in Germany is another data breach monitoring service. I only discovered it yesterday via this tweet from Per Thorsheim.
The service hosts nearly 8.2 billion accounts from 810 data leaks.
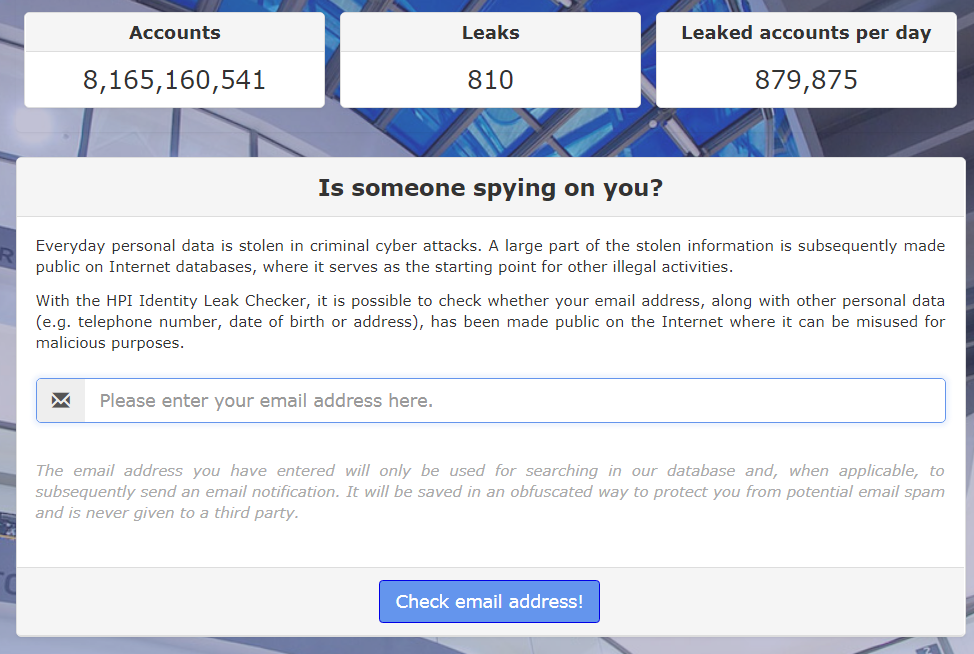
I tested it and there’s overlap with Have I Been Pwned, but also some breaches I wasn’t previously aware of. The mail you receive has a nice table with the overview of which data attributes are compromised in the data breaches.
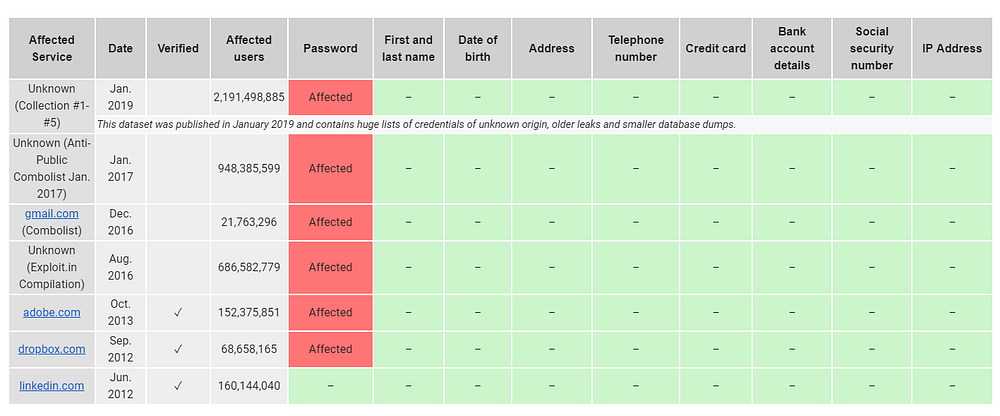
It’s not clear to me yet if they foresee subscriptions or domain monitoring like HackNotice and Have I Been Pwned do. As soon as I have more details about this I will update this article.
Browser features and extensions
Different browsers and 3rd party extensions are available to monitor for data breach exposure. They all do it in a slightly different way. Here’s a quick overview of some of them.
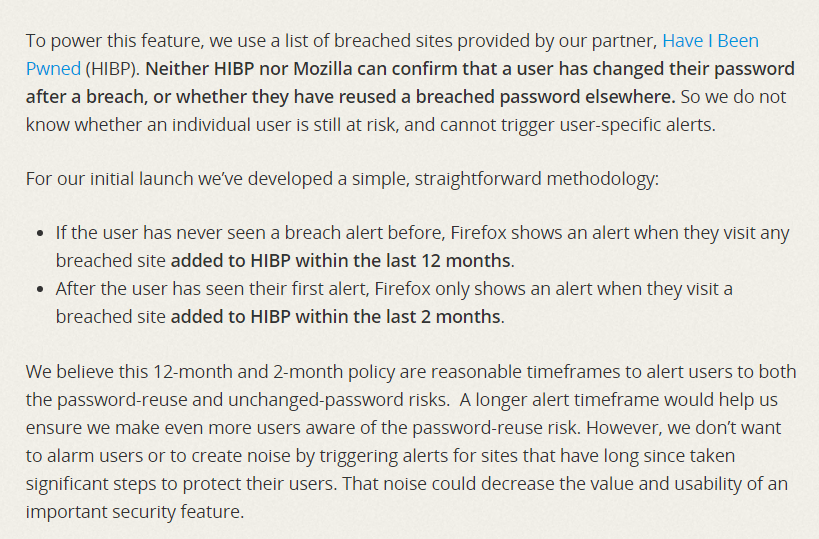
Firefox Monitor
Firefox released Firefox monitor at the end of last year. You can subscribe here for this service that uses Have I Been Pwned under the hood. The screenshot below is an excerpt from Mozilla’s blogpost. This service show alerts only when you visit a recently breached site.
Google Password Checkup
Earlier this week on Safer Internet Day google released a chrome extension it named “Password Checkup”. It can be installed via chrome’s webstore.
It uses Google’s own database containing 4 billion leaked credentials. This extension does check if the combination of username and password provided by the user have been found in the set of leaked data.
Okta Plugin
Another, yet different, kind of plugin is Okta’s Passprotect. It uses Troy Hunt’s Pwned Passwords, a set of 550 million breached passwords and alerts you via a pop up when you enter a breached password in a login form.
Other options
A trick I started using some time ago is creating application specific email aliases for each account I register. I also retroactively changed the email addresses for my existing accounts into the corresponding application specific aliases. It can help to discover the source of data breaches and spam operations in some cases. In this post you can read more about how it works.
The best thing you can do to improve your account security is using a password manager. It doesn’t matter which one you use, they all have the option to generate long, random and thus unique passwords. And not only to generate them, but most importantly to remember and recall them when necessary, at account login.
A lot of password managers are free. The one I’m using for many years now, is 1Password. It is a paying one, but it has some neat additional security features. One of them is called WatchTower. You can see on the website which functionality it offers, but when you have a license it’s integrated into 1Password and it will warn you when you’re using a password that’s known to be breached or when you’re still using the breached password on a compromised website.
Conclusion
When it comes to data breach monitoring there is no silver bullet. Even by combining several data breach notification tools and services you’ll never cover all the data breaches you’re in.
Besides, monitoring is only a detective control and by no means an excuse for sloppy account management security practices. It is an important part of your account security strategy though. If you use unique and strong passwords and 2FA were possible, the combination of all these measures will put you in the securest possible position.
If you have other tools or tips to monitor data breach exposure please share via the comments.