Like I’ve written in my previous blog a healthy dose of suspicion can help to make better security decisions.
Whenever I doubt about the security of a particular URL I use online scanning tools like VirusTotal or urlscan.io. Whilst this is absolutely a good practice, it is certainly not totally risk-free.
Most of these tools show a number of recent scan results.
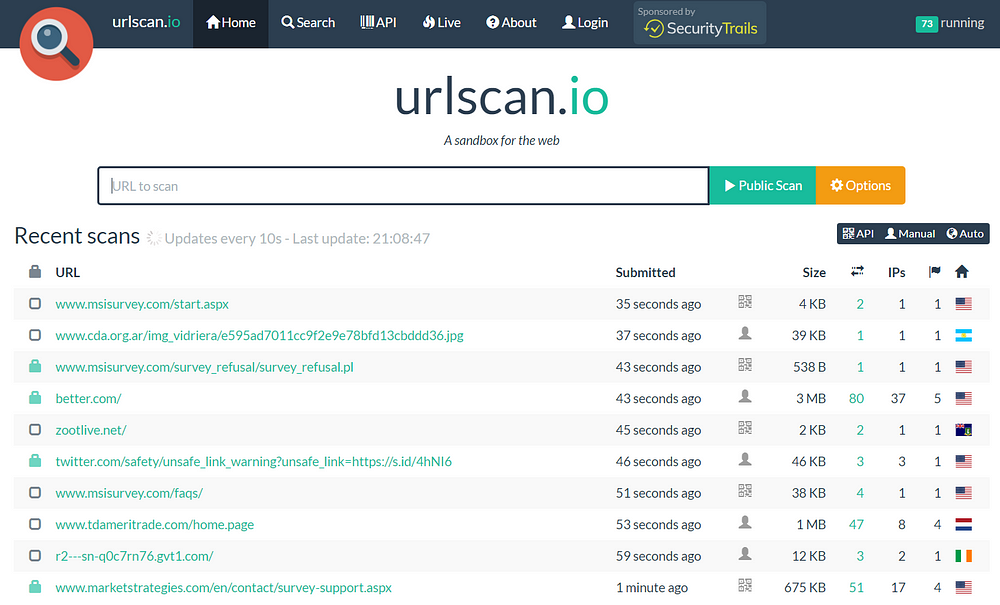
Or even offer search functionality
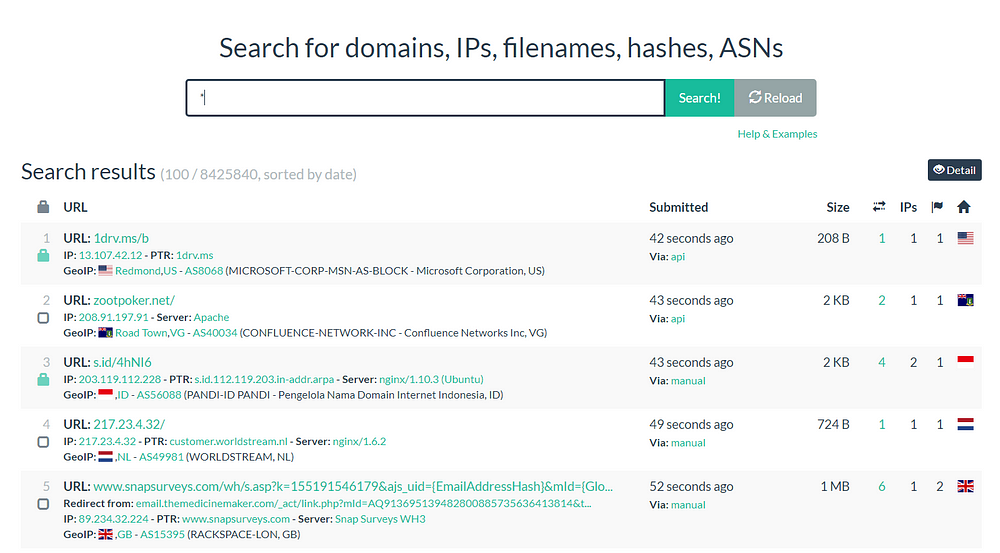
As long as you scan public links there’s no problem. But if you scan links that give — directly or indirectly — access to confidential personal data it can have serious consequences.
For instance URLs that contain session IDs. In the example below miscreants could impersonate this particular user via his Yahoo account or even take over his account.
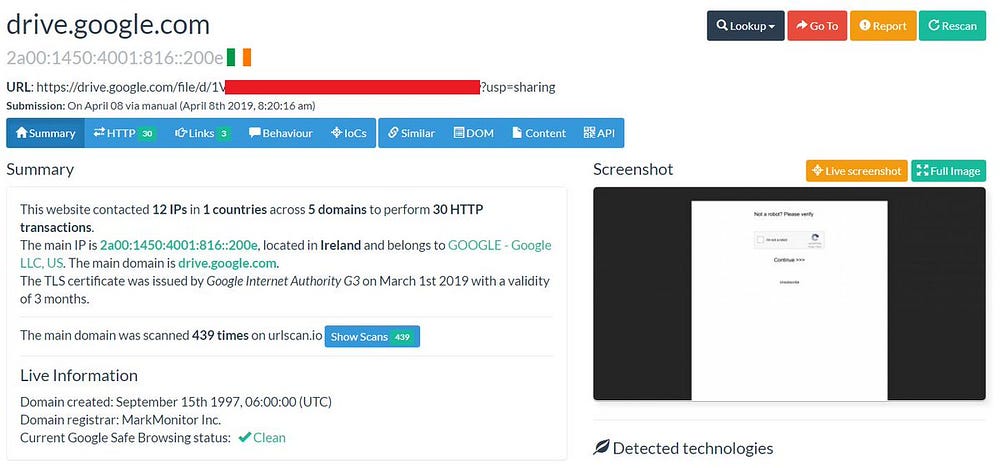
Another example are so-called unguessable URLs that are often used for file sharing purposes. They “secure” the underlying resources based on the premise that these URLs are random and only known by the system providing them and the intended recipient. They don’t offer any form of authorization.
In the screenshot below we see such an unguessable URL, a Google Drive file share, leaked via urlscan.io.
Another scanning tool I frequently use is SSL Labs. It’s really good at checking if TLS is configured securely on web servers. What a lot of people seem to forget is that SSL Labs also displays the last 10 worst websites.

And that’s for instance how I noticed that this internal server from the Philippine government is vulnerable to the Poodle Attack.

How to prevent data leakage?
Whenever you use online scanning tools, try to keep the following in mind.
- Never scan resources that host personal information or that contain session identifiers, unguessable links,… with public scanning tools.
- Preferably use tools that support private scanning mode.
Some examples…