With the blogs in this series I want to reach not only my typical audience, security professionals, but especially less security aware people to help them improve their personal security. If you think the content is helpful for people you know, share it with them!
In yesterday's post I explained how to create strong passwords and why this is so important. If you missed that post, I recommend you to read it first.
Like I said in that post, you should use unique passwords for all of your accounts. It means that when your password for one account is leaked attackers can only gain access to that particular account.
But for a lot of websites and apps you can even go one step further and activate additional layers of protection for your user account. This is referred to as multi factor authentication or in short MFA.
What it means in simple words is that in order to authentice (= login) to a website or app you need to be able to provide multiple factors (= pieces of evidence) to prove that it's really you.
The most common form is two factor authentication (2FA). You must provide 2 different pieces of evidence before you're granted access. The first piece of evidence is the usual password or pin code, something you know. But like we have seen potentially attackers know this as well. That's why on top of that it's wise to use another piece of verification and this can not be something you know, but it should be something you have.
This second factor can be a text message you receive or a code generated by an app on your smartphone.

Or even a (physical) security key

A factor can also be something you are, for instance your fingerprint or your iris pattern.
Most common implementations of 2FA and which one to use
Most online services foresee one of the following forms of 2FA. There are more but I limit myself here to the most common ones.
- SMS based
- Software tokens generated via an authenticator app (on your smartphone)
- Security keys
Security keys are the most secure ones but they are also the most expensive ones and only available for a limited amount of online services. For the average user an authenticator app is the best choice. But this option is not always available.
SMS based 2FA is vulnerable to different attacks. The most prevalent one is SIM swapping. This is when criminals convince your mobile carrier to switch your phone number over to a SIM card they own. That's why SMS based is the weakest one of these three options. But keep in mind it's still an additional barrier for attackers to gain access to your account. So if it's the only available option, enable it.
How to start
First of all you must know which sites offer 2FA. There are a few good resources that can help you. 2FA Notifier provides plugins for Chrome and Firefox. After you have installed the plugin you get notified when a website foresees 2FA. In this video made by Tanya Janca you see how to install and use the plugin.
As you see 2FA Notifier will also direct you to the documentation to configure 2FA for a particular site.
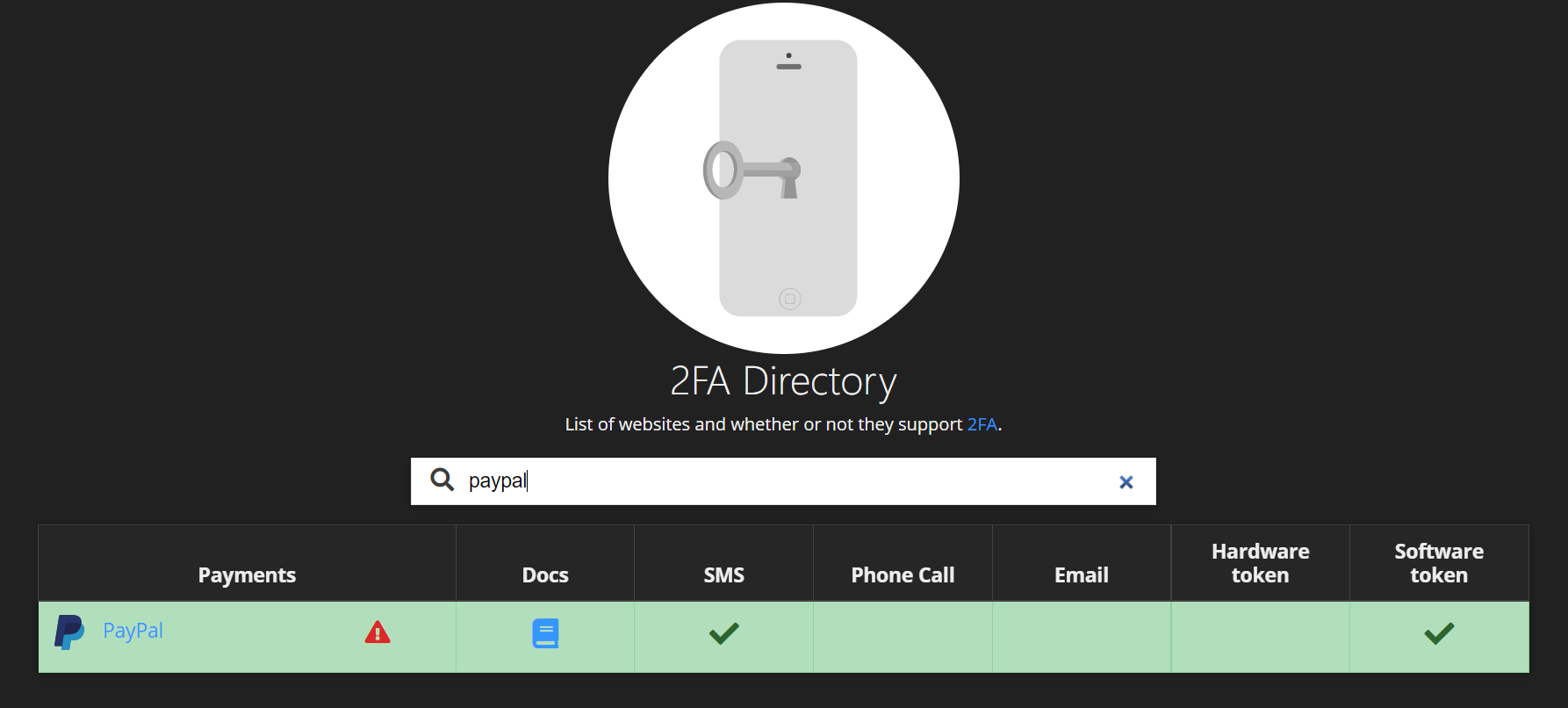
Under the hood 2FANotifier uses the following website. If you search for a particular service you see the different forms of 2FA that are supported and a link to the documentation on how to set it up.
In case of PayPal this is SMS and software tokens generated via an authenticator app. As we have seen you should opt for 2FA based on software tokens here.
If you're going to start with activating 2FA for your online accounts there are some other precautions you need to take. You'll also need to install an authenticator app. Tomorrow I'll tell you more about how you can safely configure 2FA, how authenticator apps work and what to look for when selecting one. In the meantime stay safe online!




