Earlier this week Australian security researcher Troy Hunt loaded 711 million breached accounts in Have I Been Pwned. For people that don’t know it, Have I Been Pwned is a search engine to check if your account was compromised in a data breach. You can register your e-mail address and then you get alerted when one of your accounts using that e-mail address is pwned.
Unfortunately, I was pwned again.
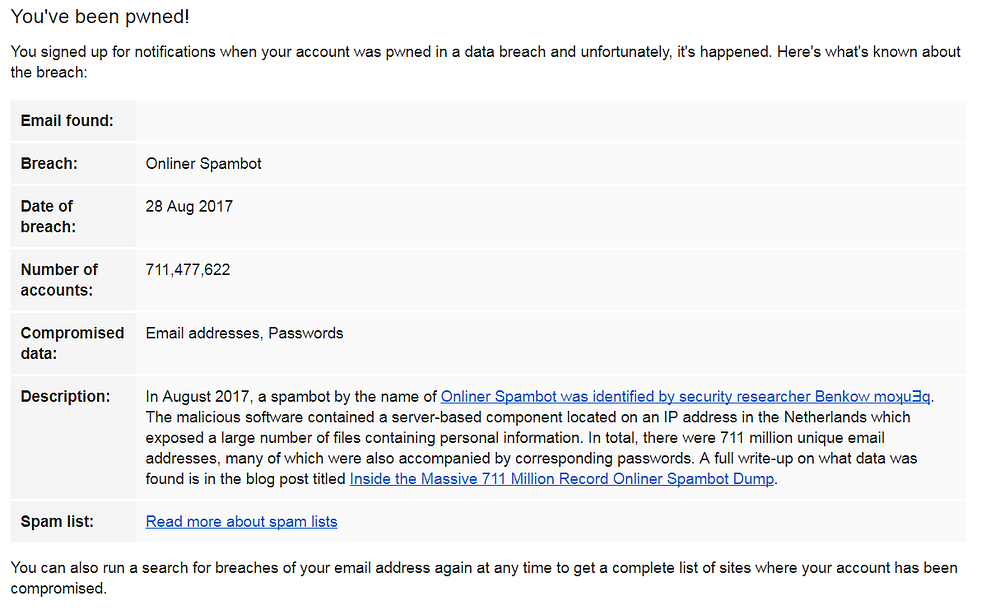
In this case e-mail addresses and in many cases the corresponding passwords were leaked. This data was used by a botnet to spread Trojans via mail attachments.
When you get to know that your credentials for a particular application are breached, the logical next step is to change the password for that account. But in this case it’s different. You don’t know which account was compromised. So there is not a lot you can do. Right?
You could reset passwords for all your accounts. But I — and I guess a lot of people as well — don’t know every application I ever registered for. Besides that, it is a really time consuming job. I think it’s an overreaction, at least if you use a well-considered strategy to manage and secure your online accounts.
Some tips to manage your online accounts securely
Use for every online application a different password. In this way you prevent that someone can (ab)use the leaked credentials to log on to your other accounts. Enable 2 factor authentication (2FA) on all applications that offer this option. This reduces the chances of abuse to a minimum.
If you do this, the worst-case scenario is abuse of a hacked account without 2FA. Not knowing which account is breached, is still an uncomfortable feeling, but at least you can exclude several accounts.
You can even go a step further. E-mail providers like Gmail offer the possibility to create aliases for an e-mail address. If your e-mail address is “[email protected]”, you could use at the registration of your facebook account “[email protected]”. The e-mails still arrives in your “[email protected]” mailbox. For existing accounts you can also change the e-mail address to an application specific alias.
When you apply this principle consistently, you can identify which application is hacked via the e-mail address.
Is it really necessary to use your ‘real’ e-mail address?
Today I received a mail from a Radio station while I never gave them my e-mail address. Most likely because I created an account for a related news site. It really annoys me that I unwillingly receive such e-mails and that I don’t know how they got my e-mail address. And yes I know, if I had subscribed myself with an application specific alias at the time I would have known the reason for this unsolicited mail…
On the other hand, we can be a little bit more thoughtful when creating an account. Let’s say you want to create an account for the website of the local newspaper. You could use the e-mail address you also use for your other, more important accounts. But you might as well use a “throwaway” e-mail address, for example mailinator.
You just make up an e-mail address, for example “[email protected]”, go to the mailinator website and enter it.
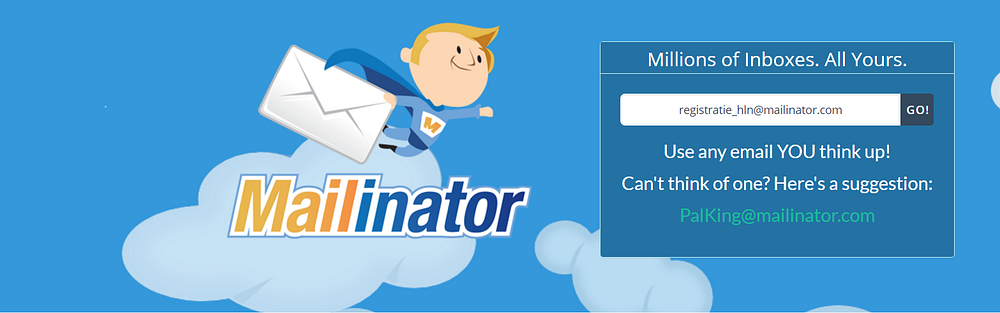
You immediately have access to this mailbox. There is no need to go through a registration process.
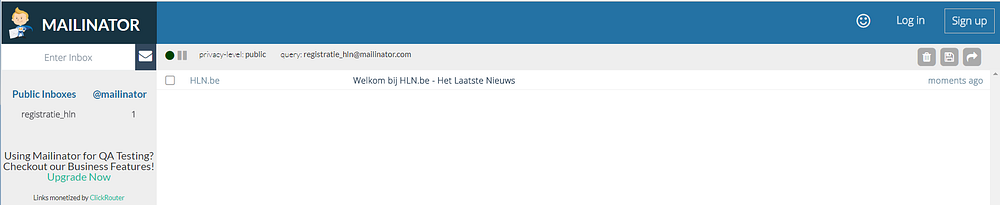
Messages in a mailinator inbox are kept for only a few hours and are accessible by anyone who enters this same e-mail address. Use mailinator (or alternatives) only for scenarios like account activation on sites where you don’t enter personal information.
In this way you disclose a little bit less personal data and as an extra advantage your “real” e-mail account gets less spam, erm I mean “marketing” e-mails.

